Title: Security Accounts Manager | Author: clark@hushmail.com | Last updated: 3rd April 2005
This article is based primarily on a local default setup of NT5.0 Professional or 2K (Windows 2000), however there maybe additional verified references to XP Professional and Server Editions. Much will apply across the NT range, but not all has been verified. Note that this is a partial update from the orginal version, there will be more additions, I just thought it was time to consolidate some stuff. This article has been written concisely and progressively, it is advisable not to skim read. Some stuff is advanced, use a test machine where possible.
Special thanks to: (alphabetically ordered)
esrever_otua: For pointing out something which I had missed about group memberships.
fishy5: For coding XORCheck.exe which calculates the registry hive checksum.
mirrorshades: For inspiring a hash database space optimzation technique
rattle: For coding ntdate.exe which calculates the NT time format and the LastPolicyTime; a couple of programs for the #DAD8636F687BF15B
section and for working on the LM Hash Decoder V1/V2 projects.
Serg Wasilenkow: For working on the LM Hash Decoder V1/V2 projects.
Vladimir Katalov: For the PWSEx product key and working on the LM Hash Decoder V1/V2 projects.
xavic: For inspiring a hash database space optimzation technique
Due to length and my decision not to divide this article into separate pages I have split the article into 4 main chapters.
01. Users and Groups
02. (some) Security Settings
03. Registry Structure
04. Passwords
Within these chapters are sections divided by a dotted horizontal line. To the left of this line is an image like so:  These are anchors. These are anchors.
If you right-click on them you can copy the shortcut/link address or left-click (IE only) and add it directly to your bookmarks.
These bookmarks may change so I have used random hex as the link - make sure you name the link appropriatley.
Users can be added via a MMC with the "Local Users and Groups" Snap-in being present (Windows includes two such MMCs; compmgmt.msc and lusrmgr.msc) or via the [Add...] button in "Users and Passwords" - found in Control Panel. (Active Directory is configured via the Active Directory Users and Computers Snap-in or dsa.msc) Also via CMD: C:\>net user %username% /add
Another way that is usually forgotten is the Network Identification Wizard that shows up once when installing the 2K operating system. On running it checks the current users, normally just Guest and Administrator and it also checks the RegisteredOwner value located here: \HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\ that was just entered earlier in the setup. If an account has not been created for the user listed, an administrative level one can be created here. Note you cannot overwrite passwords of existing accounts. To re-trigger this dialog, boot from Petter Nordahl-Hagen's boot disk:
Load the SOFTWARE hive
Cd to \Microsoft\Windows NT\CurrentVersion\
Ed RegisteredOwner value; if an account is already created by that name or if a different one is required.
Cd to \Winlogon\
Nv 4 RunNetAccessWizard
Ed RunNetAccessWizard = 0x1
On reboot keep the selection on Windows always assumes the following user has logged onto this computer: user name from dropdown list should be the RegisteredOwner, enter a password, next, finish. The user will be automatically logged on. Remember to uncheck: Users must enter a user name and password to use this computer. In the Users and Password in Control Panel. Also remember that since this method uses the secure autologon feature any existing autologon credentials will be overwritten, this will probably not be a problem however.
This method also works in XP, however the process is alittle more complex. If there are three or more Administrator/(power)users accounts collectivily present, users cannot be added via the re-triggered dialog, this is likely to be the case, hence you have to make it believe otherwise. If there are two or less, skip the SAM editing sections. Boot from Petter Nordahl-Hagen's boot disk:
Load the SAM and SYSTEM hives
Cd to \SYSTEM\Setup\
Ed SetupType = 0x2
Ed CmdLine = c:\windows\system32\oobe\msoobe.exe /f /retail (FYI: Just /f = full setup; license, key, activation & users)
Nv 4 OobeInProgress
Ed OobeInProgress = 0x1
Switch to the SAM hive.
Cd to \SAM\SAM\Domains\Builtin\Aliases\00000220\C (Administrators)
Cd to \SAM\SAM\Domains\Builtin\Aliases\00000221\C (Users)
Cd to \SAM\SAM\Domains\Builtin\Aliases\00000223\C (Power Users)
Make a note of the 4 bytes at offset 2C and 30, check the first user number in 00000220 after the description is F4,01,00,00 (most likely)
Edit the C values at both offsets for 00000220 & 00000221 with 00,00,00,00 - for 00000223: :2c 18 00 00 00 & :30 02 00 00 00
Save and reboot. Add a user (upto five can be added here, all at administratove level) and logon with that user name using a blank password. Run regedit.exe and write back the 00000221 and 00000223 C values. Amend the 00000220 C key, make a note of the new user number that has overwritten the orginal (F4,01,00,00) one, restore to orginal and add a similar 28 byte entry at the end in the nulls provided with the current user number after the machine SID. Reboot to complete.
Another unorthodox method is to run the net command as a service. Boot from Petter Nordahl-Hagen's boot disk and load the SYSTEM hive. cd to \CurrentControlSet001\Services\ create a two keys for the two commands. The editor seems to have a slight bug in that keys cannot be created that are prefixed with an existing service name, eg: error on creating a key named foobar if a key named foo exists. Remember that the services will be processed in alphabetical order.
Cd in the first alpha newly created key.
Nv 4 ErrorControl
Ed ErrorControl = 0x1
Nv 2 ImagePath
Ed ImagePath = %systemroot%\system32\net.exe user foo /add
Nv 1 ObjectName
Ed ObjectName = LocalSystem
Nv 4 Start
Ed Start = 0x2
Nv 4 Type
Ed Type = 0x20
Cd in the second alpha newly created key.
Repeat the steps above, but with:
Ed ImagePath = %systemroot%\system32\net.exe localgroup administrators foo /add
Reboot and login, remove the keys. 2K creates a couple of system error event log so this may need removing.
One method that is often mentioned, that does not seem to work (anymore(?)) is changing the default screensaver to a program that allows usermanagement like cmd.exe or mmc.exe The settings are located here:
regedit.exe -> \HKEY_USERS\.DEFAULT\Control Panel\Desktop\
explorer.exe -> \%windir%\system32\config\DEFAULT
SCRNSAVE.EXE=logon.scr - This is the screensave that will be used if nobody logs on locally for awhile.
ScreenSaveActive=1 - Active=1 Inactive=0
ScreenSaveTimeOut=600 - Number of idle seconds before screensaver activation (5mins)
ScreenSaverIsSecure=0 - This is the "On resume, password protect" option. Curious this option though, some kind of memory limit if set to 0. Important to note if more memory is used.
However even if you update logon.scr the SYSTEM user, which is who you will be while the "Winlogon generic control dialog" lurks in the background, does not have permission to add or modify any users - System error 5 has occured
Access is denied. If a user logs on, SYSTEM does have access, so some kind of security assumed before logon. It maybe possible using a custom program, certainly with access to regedit.exe a user could be added manually.
The SID number is used in file, registry, service and users permissions. The machine SID is determined in hexidecimal form from here:
regedit.exe -> \HKEY_LOCAL_MACHINE\SAM\SAM\Domains\Account\V (last 12 bytes)
explorer.exe -> \%windir%\system32\config\SAM
If the SAM file is missing at startup, a backup is retrieved in hexidecimal form here:
regedit.exe -> \HKEY_LOCAL_MACHINE\SECURITY\Policy\PolAcDmS\@ (last 12 bytes)
explorer.exe -> \%windir%\system32\config\SECURITY
Sometimes the SID number is referenced in decimal form:
|
|
| 2E,43,AC,40,C0,85,38,5D,07,E5,3B,2B | |
| 1) Divide the bytes into 3 sections: | |
| 2E,43,AC,40 , C0,85,38,5D , 07,E5,3B,2B | |
| 2) Reverse the bytes of each section: | |
| 40,AC,43,2E , 5D,38,85,C0 , 2B,3B,E5,07 | |
| 3) Convert each section into decimal: | |
| 1085031214 , 1563985344 , 725345543 | |
| 4) Add the machine SID prefix: | |
| S-1-5-21-1085031214-1563985344-725345543 | | S-1-5-21-1085031214-1563985344-725345543 - This is the machine SID number in decimal format.
NT stored time format is referenced in user keys, registry hives etc. The precision is to a very small fraction of a second from 1601.
100,000 = one millisecond
10,000,000 = one second
600,000,000 = one minute
36,000,000,000 = one hour
864,000,000,000 = one day
date time debug view reversed view decimal
01/01/1601 - 12:00 AM = 00,00,00,00,00,00,00,00 -> 00,00,00,00,00,00,00,00 -> 0
01/01/2000 - 12:00 AM = 00,40,6D,25,EB,53,BF,01 -> 01,BF,53,EB,25,6D,40,00 -> 125,911,584,000,000,000
01/01/2001 - 12:00 AM = 00,C0,9D,C8,85,73,C0,01 -> 01,C0,73,85,C8,9D,C0,00 -> 126,227,808,000,000,000
01/01/2002 - 12:00 AM = 00,80,64,41,57,92,C1,01 -> 01,C1,92,57,41,64,80,00 -> 126,543,168,000,000,000
01/01/2003 - 12:00 AM = 00,40,2B,BA,28,B1,C2,01 -> 01,C2,B1,28,BA,2B,40,00 -> 126,858,528,000,000,000
01/01/2004 - 12:00 AM = 00,00,F2,32,FA,CF,C3,01 -> 01,C3,CF,FA,32,F2,00,00 -> 127,173,888,000,000,000
03/21/2004 - 12:00 AM = 00,00,FE,73,D7,0E,C4,01 -> 01,C4,0E,D7,73,FE,00,00 -> 127,243,008,000,000,000
To save time in calculating this value use ntdate.exe
|
|
|
|
2000 Professional
2000 Server
2000 Server with Active Directory
XP Home
XP Professional
2003 Server
2003 Server with Active Directory | |
|
| |
|
The codes in the table to the left are used in the below table in the far right column.
Treat the OS column as an approximate guide as it depends on the configuration of the OS.
The 2 character code eg, WD is used in the policy infs or security templates.
Where -> is used, there is no 2 character code, the SID is used instead.
Users RID's can be from 1000 or 1100 depending which OS is installed/upgraded.
The hexidecimal code is used in the registry, NTFS and services permissions plus user groups. |
Everyone -------------------------
CREATOR OWNER --------------------
CREATOR GROUP --------------------
DIALUP ---------------------------
NETWORK --------------------------
BATCH ----------------------------
INTERACTIVE ----------------------
SERVICE --------------------------
ANONYMOUS LOGON ------------------
PROXY ----------------------------
ENTERPRISE DOMAIN CONTROLLERS ----
SELF -----------------------------
Authenticated Users --------------
RESTRICTED -----------------------
TERMINAL SERVER USER -------------
REMOTE INTERACTIVE LOGON ---------
This Organization ----------------
SYSTEM ---------------------------
LOCAL SERVICE --------------------
NETWORK SERVICE ------------------
Administrator (builtin) ----------
Guest (builtin) ------------------
krbtgt ---------------------------
Domain Admins --------------------
Domain Users ---------------------
Domain Guests --------------------
Domain Computers -----------------
Domain Controllers ---------------
Schema Admins --------------------
Cert Publishers ------------------
Enterprise Admins ----------------
Group Policy Creator Owners ------
RAS and IAS Servers --------------
DHCP Administrators --------------
DHCP Users -----------------------
DnsAdmins ------------------------
DnsUpdateProxy -------------------
HelpAssistant --------------------
HelpServicesGroup ----------------
SUPPORT_xxxxxxxx -----------------
ASPNET ---------------------------
ILS_ANONYMOUS_USER ---------------
IUSR_%machinename% ---------------
IWAM_%machinename% ---------------
IIS_WPG --------------------------
NetShow Administrators -----------
NetShowServices ------------------
TelnetClients --------------------
Terminal Server Computers --------
TsInternetUser -------------------
WINS Users -----------------------
WMUS_%machinename% ---------------
%Specific User% ------------------
%Custom Group% -------------------
Administrators -------------------
Users ----------------------------
Guests ---------------------------
Power Users ----------------------
Account Operators ----------------
Server Operators -----------------
Print Operators ------------------
Backup Operators -----------------
Replicator -----------------------
Pre-Windows 2000 Compatible Access
Remote Desktop Users -------------
Network Configuration Operators --
Incoming Forest Trust Builders ---
Performance Monitor Users --------
Performance Log Users ------------
Windows Authorization Access Group
Terminal Server License Servers --
NTLM Authentication --------------
SChannel Authentication ----------
Digest Authentication ------------
Other Organization --------------- | |
WD
CO
CG
->
NU
->
IU
SU
->
->
ED
PS
AU
RC
->
->
->
SY
LS
NS
LA
LG
->
DA
DU
DG
DC
DD
SA
CA
EA
PA
RS
->
->
->
->
->
->
->
->
->
->
->
->
->
->
->
->
->
->
->
->
->
BA
BU
BG
PU
AO
SO
PO
BO
RE
RU
RD
NO
->
->
->
->
->
->
->
->
-> | |
S-1-1-0 ------------
S-1-3-0 ------------
S-1-3-1 ------------
S-1-5-1 ------------
S-1-5-2 ------------
S-1-5-3 ------------
S-1-5-4 ------------
S-1-5-6 ------------
S-1-5-7 ------------
S-1-5-8 ------------
S-1-5-9 ------------
S-1-5-10 -----------
S-1-5-11 -----------
S-1-5-12 -----------
S-1-5-13 -----------
S-1-5-14 -----------
S-1-5-15 -----------
S-1-5-18 -----------
S-1-5-19 -----------
S-1-5-20 -----------
S-1-5-21-%SID%-500 -
S-1-5-21-%SID%-501 -
S-1-5-21-%SID%-502 -
S-1-5-21-%SID%-512 -
S-1-5-21-%SID%-513 -
S-1-5-21-%SID%-514 -
S-1-5-21-%SID%-515 -
S-1-5-21-%SID%-516 -
S-1-5-21-%SID%-518 -
S-1-5-21-%SID%-517 -
S-1-5-21-%SID%-519 -
S-1-5-21-%SID%-520 -
S-1-5-21-%SID%-553 -
S-1-5-21-%SID%-%RID%
S-1-5-21-%SID%-%RID%
S-1-5-21-&SID%-%RID%
S-1-5-21-&SID%-%RID%
S-1-5-21-%SID%-%RID%
S-1-5-21-%SID%-%RID%
S-1-5-21-%SID%-%RID%
S-1-5-21-%SID%-%RID%
S-1-5-21-%SID%-%RID%
S-1-5-21-%SID%-%RID%
S-1-5-21-%SID%-%RID%
S-1-5-21-%SID%-%RID%
S-1-5-21-%SID%-%RID%
S-1-5-21-%SID%-%RID%
S-1-5-21-%SID%-%RID%
S-1-5-21-%SID%-%RID%
S-1-5-21-%SID%-%RID%
S-1-5-21-%SID%-%RID%
S-1-5-21-%SID%-%RID%
S-1-5-21-%SID%-%RID%
S-1-5-21-%SID%-%RID%
S-1-5-32-544 -------
S-1-5-32-545 -------
S-1-5-32-546 -------
S-1-5-32-547 -------
S-1-5-32-548 -------
S-1-5-32-549 -------
S-1-5-32-550 -------
S-1-5-32-551 -------
S-1-5-32-552 -------
S-1-5-32-554 -------
S-1-5-32-555 -------
S-1-5-32-556 -------
S-1-5-32-557 -------
S-1-5-32-558 -------
S-1-5-32-559 -------
S-1-5-32-560 -------
S-1-5-32-561 -------
S-1-5-64-10 --------
S-1-5-64-14 --------
S-1-5-64-21 --------
S-1-5-1000 --------- | |
01,01,000000000001,00000000---------------------------------
01,01,000000000003,00000000---------------------------------
01,01,000000000003,01000000---------------------------------
01,01,000000000005,01000000---------------------------------
01,01,000000000005,02000000---------------------------------
01,01,000000000005,03000000---------------------------------
01,01,000000000005,04000000---------------------------------
01,01,000000000005,06000000---------------------------------
01,01,000000000005,07000000---------------------------------
01,01,000000000005,08000000---------------------------------
01,01,000000000005,09000000---------------------------------
01,01,000000000005,0A000000---------------------------------
01,01,000000000005,0B000000---------------------------------
01,01,000000000005,0C000000---------------------------------
01,01,000000000005,0D000000---------------------------------
01,01,000000000005,0E000000---------------------------------
01,01,000000000005,0F000000---------------------------------
01,01,000000000005,12000000---------------------------------
01,01,000000000005,13000000---------------------------------
01,01,000000000005,14000000---------------------------------
01,05,000000000005,15000000,xxxxxxxxxxxxxxxxxxxxxxxx,F4010000
01,05,000000000005,15000000,xxxxxxxxxxxxxxxxxxxxxxxx,F5010000
01,05,000000000005,15000000,xxxxxxxxxxxxxxxxxxxxxxxx,F6010000
01,05,000000000005,15000000,xxxxxxxxxxxxxxxxxxxxxxxx,00020000
01,05,000000000005,15000000,xxxxxxxxxxxxxxxxxxxxxxxx,01020000
01,05,000000000005,15000000,xxxxxxxxxxxxxxxxxxxxxxxx,02020000
01,05,000000000005,15000000,xxxxxxxxxxxxxxxxxxxxxxxx,03020000
01,05,000000000005,15000000,xxxxxxxxxxxxxxxxxxxxxxxx,04020000
01,05,000000000005,15000000,xxxxxxxxxxxxxxxxxxxxxxxx,06020000
01,05,000000000005,15000000,xxxxxxxxxxxxxxxxxxxxxxxx,05020000
01,05,000000000005,15000000,xxxxxxxxxxxxxxxxxxxxxxxx,07020000
01,05,000000000005,15000000,xxxxxxxxxxxxxxxxxxxxxxxx,08020000
01,05,000000000005,15000000,xxxxxxxxxxxxxxxxxxxxxxxx,29020000
01,05,000000000005,15000000,xxxxxxxxxxxxxxxxxxxxxxxx,xxxxxxxx
01,05,000000000005,15000000,xxxxxxxxxxxxxxxxxxxxxxxx,xxxxxxxx
01,05,000000000005,15000000,xxxxxxxxxxxxxxxxxxxxxxxx,xxxxxxxx
01,05,000000000005,15000000,xxxxxxxxxxxxxxxxxxxxxxxx,xxxxxxxx
01,05,000000000005,15000000,xxxxxxxxxxxxxxxxxxxxxxxx,xxxxxxxx
01,05,000000000005,15000000,xxxxxxxxxxxxxxxxxxxxxxxx,xxxxxxxx
01,05,000000000005,15000000,xxxxxxxxxxxxxxxxxxxxxxxx,xxxxxxxx
01,05,000000000005,15000000,xxxxxxxxxxxxxxxxxxxxxxxx,xxxxxxxx
01,05,000000000005,15000000,xxxxxxxxxxxxxxxxxxxxxxxx,xxxxxxxx
01,05,000000000005,15000000,xxxxxxxxxxxxxxxxxxxxxxxx,xxxxxxxx
01,05,000000000005,15000000,xxxxxxxxxxxxxxxxxxxxxxxx,xxxxxxxx
01,05,000000000005,15000000,xxxxxxxxxxxxxxxxxxxxxxxx,xxxxxxxx
01,05,000000000005,15000000,xxxxxxxxxxxxxxxxxxxxxxxx,xxxxxxxx
01,05,000000000005,15000000,xxxxxxxxxxxxxxxxxxxxxxxx,xxxxxxxx
01,05,000000000005,15000000,xxxxxxxxxxxxxxxxxxxxxxxx,xxxxxxxx
01,05,000000000005,15000000,xxxxxxxxxxxxxxxxxxxxxxxx,xxxxxxxx
01,05,000000000005,15000000,xxxxxxxxxxxxxxxxxxxxxxxx,xxxxxxxx
01,05,000000000005,15000000,xxxxxxxxxxxxxxxxxxxxxxxx,xxxxxxxx
01,05,000000000005,15000000,xxxxxxxxxxxxxxxxxxxxxxxx,xxxxxxxx
01,05,000000000005,15000000,xxxxxxxxxxxxxxxxxxxxxxxx,xxxxxxxx
01,05,000000000005,15000000,xxxxxxxxxxxxxxxxxxxxxxxx,xxxxxxxx
01,02,000000000005,20000000,20020000------------------------
01,02,000000000005,20000000,21020000------------------------
01,02,000000000005,20000000,22020000------------------------
01,02,000000000005,20000000,23020000------------------------
01,02,000000000005,20000000,24020000------------------------
01,02,000000000005,20000000,25020000------------------------
01,02,000000000005,20000000,26020000------------------------
01,02,000000000005,20000000,27020000------------------------
01,02,000000000005,20000000,28020000------------------------
01,02,000000000005,20000000,2A020000------------------------
01,02,000000000005,20000000,2B020000------------------------
01,02,000000000005,20000000,2C020000------------------------
01,02,000000000005,20000000,2D020000------------------------
01,02,000000000005,20000000,2E020000------------------------
01,02,000000000005,20000000,2F020000------------------------
01,02,000000000005,20000000,30020000------------------------
01,02,000000000005,20000000,31020000------------------------
01,02,000000000005,40000000,0A000000------------------------
01,02,000000000005,40000000,0E000000------------------------
01,02,000000000005,40000000,15000000------------------------
01,01,000000000005,E8030000--------------------------------- | |
2p,2s,2a,xh,xp,3s,3a
2p,2s,2a,xh,xp,3s,3a
2p,2s,2a,xh,xp,3s,3a
2p,2s,2a,xh,xp,3s,3a
2p,2s,2a,xh,xp,3s,3a
2p,2s,2a,xh,xp,3s,3a
2p,2s,2a,xh,xp,3s,3a
2p,2s,2a,xh,xp,3s,3a
2p,2s,2a,xh,xp,3s,3a
------2a----------3a
------2a----------3a
------2a----------3a
2p,2s,2a,xh,xp,3s,3a
------2a----------3a
2p,2s,2a,xh,xp,3s,3a
---------xh,xp,3s,3a
------------------3a
2p,2s,2a,xh,xp,3s,3a
---------xh,xp,3s,3a
---------xh,xp,3s,3a
2p,2s,2a,xh,xp,3s,3a
2p,2s,2a,xh,xp,3s,3a
------2a----------3a
------2a----------3a
------2a----------3a
------2a----------3a
------2a----------3a
------2a----------3a
------2a----------3a
------2a----------3a
------2a----------3a
------2a----------3a
------2a----------3a
------2a----------3a
------2a----------3a
------2a----------3a
------2a----------3a
---------xh,xp------
---------xh,xp,3s,3a
---------xh,xp,3s,3a
2p,2s,2a,xh,xp------
------2a------------
---2s,2a----xp,3s,3a
---2s,2a----xp,3s,3a
---------------3s,3a
------2a------------
------2a------------
---------------3s,3a
------------------3a
---2s,2a------------
------2a------------
------------------3a
2p,2s,2a,xh,xp,3s,3a
2p,2s,2a,xh,xp,3s,3a
2p,2s,2a,xh,xp,3s,3a
2p,2s,2a,xh,xp,3s,3a
2p,2s,2a,xh,xp,3s,3a
2p,2s,2a----xp,3s,3a
------2a----------3a
------2a----------3a
------2a-------3s,3a
2p,2s,2a----xp,3s,3a
2p,2s,2a----xp,3s,3a
------2a----------3a
------------xp,3s,3a
------------xp,3s,3a
------------------3a
---------------3s,3a
---------------3s,3a
------------------3a
------------------3a
------------------3a
------------------3a
------------------3a
------------------3a | |
 |
| When a user is added, the following keys are added: \HKEY_LOCAL_MACHINE\SAM\SAM\Domains\Account\Users\Names\%username%\@ This key determines the login name. File location: C:\WINNT\system32\config\SAM The @ value holds a number which matches up to a 8 digit number (nulls are prefixed if less than 8) located here: HKEY_LOCAL_MACHINE\SAM\SAM\Domains\Account\Users\%00000XXX%\ Within are two REG_BINARY values; F and V.
As mentioned before user numbers start from 1000. There are a couple of builtin accounts that start from 500. Since security permissions are determined by user number, no two users should ever have the same number. User number increment and are not reused when a user is deleted. A record of this is kept here: \HKEY_LOCAL_MACHINE\SAM\SAM\Domains\Account\F Offset:48 - length:4 - Stored in reverse hex. This is the next user number that will be used. When is value reaches FF,FF,FF,FF it will rollback and starting incrementing from 00,00,00,00. 4,294,967,296 maximum accounts. Note that if a large number of accounts are used, a rather high spec machine will be required to make it viable.
All user numbers are also listed here: HKEY_LOCAL_MACHINE\SAM\SAM\Domains\Account\Groups\00000201\C
After: NoneOrdinary users - lists the user numbers at the end, like a group C value.
Offset: 3C - length: 4bytes = length of user list (reverse hex)
Offset: 40 - length: 4bytes = number of users (reverse hex)
The system allocates 100 byte blocks that hold 25 user accounts 4 byte usernumber, padded with nulls if not all used.
User 00,00,00,00 cannot logon: Logon Message
The system cannot log you on due to the following error:
The system cannot find the message text for message number 0x%1 in the message file for %2.
Please try again or consult your system administrator. Due to the way the registry is handled at hex level, user accounts 00,00,00,00 to 00,00,00,0B do not display their \HKEY_LOCAL_MACHINE\SAM\SAM\Domains\Account\Users\Names\%username%\@ value type correctly:
00/00 - REG_NONE
01/01 - REG_SZ*
02/02 - REG_EXPAND_SZ
03/03 - REG_BINARY*
04/04 - REG_DWORD
05/05 - REG_DWORD_LITTLE_ENDIAN
06/06 - REG_LINK
07/07 - REG_MULTI_SZ
08/08 - REG_RESOURCE_LIST
09/09 - REG_FULL_RESOURCE_DESCRIPTOR
10/0A - REG_RESOURCE_REQUIREMENTS_LIST
11/0B - REG_QWORD
On attempting to delete accounts 0-999: Local Users and Groups
The following error occurred while attempting to delete the user %username:
Cannot perform this operation on builtin-in accounts.
If the user counter has the same number as an existing user (this should not *normally* happen) the following error message is shown: Local Users and Groups
The following error occured while attempting to create user %username% on computer %computername%
The user already belongs to this group. (More help is available by typing NET HELPMSG 2236)
User 00,00,01,F6 (502) cannot logon: Logon Message
Your account has been disabled. Please see your system administrator. This is because this usernumber is already used by the system, krbtgt = Key Distribution Center Service Account - though I thought this was only for server edition. The account is disabled/inactive and cannot be enabled.
 |
| Windows XP by default uses a fluffy welcome screen to logon users. This can be bypassed to the normal one by holding down the Ctrl and Alt/Alt Gr keys and pressing the Del/Delete key twice. To switch off long term see Users Accounts in Control Panel: Change the way users log on or off. The list of users that is displayed in the Welcome screen is of note:
# Disabled/inactive accounts are not listed
# If there are no other administrators the built-in is listed, else it is not listed
# Administrators, Guests, Power Users & Users are listed
# Backup Operators, helpservicesgroup, Network Configuration Operators, Remote Desktop Users & Replicator are not listed
# User of no groups and users only member of custom groups are not listed
# In safe mode only <=2 administrators are listed, first two alphabetically from \SAM\SAM\Domains\Account\Users\Names\
\Security Settings\Local Policies\User Rights Assignment\Deny logon locally = user not listed
# Upto 100 users can be displayed, first alphabetically, as before, though things get alittle sluggish:
# \HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\LogonType=X fluffy=1 classic=0
# Specific users or users preffixed with something can be set so not to be listed, the record is here:
\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\SpecialAccounts\UserList\%username%:REG_DWORD
0x0 = exact match or 0x10000 = prefixed match
 |
| If the username in \%RID%\V does not matchup with the key name in \Names\%username% the dialog "Users and Passwords" in Control Panel does not list the username. On attempting to get the users properties in lusrmgr.msc it will error with: Local Users and Groups
The following error occurred while attempting to read the properties for the user %username%:
The user name could not be found. If you rename the account back to the orginal one, a new key is created in \Names\ - as a result of having two name keys with the same user number, both can be used to logon with. lusrmgr.msc does not list any users at this point while CMD always lists the users.
2K has an interesting minor problem with the Users and Password dialog in Control Panel creating an account using the local machine name for a username. On clicking finish, it will error with: "The user %username% could not be (granted %username% access _or_ added to the %groupname% group) because %username% does not exist" However the user is created of no group. XP and 2K3 will not allow a machine name to be set to Administrator or Guest at install.
 |
| It is possible to create a user that does not appear at all in the user management and yet still be able to logon. In this proof-of-concept I have used group policy user logon/off scripts and insecure registry permissions, ideally this would be deployed via a small program running at system level. Create a user and export and combine these two keys into a reg file and place in the logoff scripts folder:
HKEY_LOCAL_MACHINE\SAM\SAM\Domains\Account\Users\%usernumber%
HKEY_LOCAL_MACHINE\SAM\SAM\Domains\Account\Users\Names\%username%
Copy over the "Command-line registry manipulation utility" reg.exe to the system32 directory.
Create a logon script:
reg delete HKLM\SAM\SAM\Domains\Account\Users\Names\%username% /force
reg delete HKLM\SAM\SAM\Domains\Account\Users\%usernumber% /force
Create a logoff script: regedit /s user.reg
Add the scripts via gpedit.msc \Local Computer Policy\User Configuration\Windows Settings\Scripts(Logon/Logoff)
When a user logs on the user keys are removed, so the user is not seen. At logoff they are added back. Since the authentication process occurs before the keys are deleted and held in memory the user can authenticate correctly.
 |
|
User names:
C:\>net user %username% /add (can be rename via GUI, not via CMD)
Have to be >=1 and <=20. Cannot be dublicated of any existing users or groups of any case, can contain letters, numbers, special, extended and control characters. If the username or password is incorrect at logon the following error message will be displayed: Logon Message
The system could not log you on. Make sure your User name and domain are correct, then type your password again. Letters in passwords, must be typed using the correct case. Make sure that Caps Lock is not accidently on. |
Password:
C:\>net user %username% %password% - have to be >=0 and <= 256
C:\>net user %username% * (for private password entry, confirmation required to set - 3 fails: A valid password was not entered) |
Full names:
C:\>net user %username% /fullname:%fullname% - have to be >=0 and <=48CMD/256GUI |
Descriptions/Comment:
C:\>net user %username% /comment:%description% - have to be >=0 and <=48CMD/256GUI
User's comment:
C:\>net user %username% /usercomment:%usercomment% - have to be >=0 and <=48CMD/NOGUI |
Country code:
C:\>net user %username% /country:XXX
C:\>net user %username% /countrycode:XXX
Where XXX can be:
000 (System Default)
001 (United States)
002 (Canada (French))
003 (Latin America)
031 (Netherlands)
032 (Belgium)
033 (France)
034 (Spain)
039 (Italy)
041 (Switzerland)
044 (United Kingdom)
045 (Denmark)
046 (Sweden)
|
047 (Norway)
049 (Germany)
061 (Australia)
081 (Japan)
082 (Korea)
086 (China (PRC))
088 (Taiwan)
099 (Asia)
351 (Portugal)
358 (Finland)
785 (Arabic)
972 (Hebrew) |
Not sure what this affects, not displayed time or keyboard though |
Account active/Account is enabled or disabled:
C:\>net user %username% /active:yes/y/no/n
Logon Message
Your account has been disabled. Please see your system administrator. |
Account expires:
C:\>net user %username% /expires:never
C:\>net user %username% /expires:31/12/2004 (prefixed time of 12:00 AM)
Logon Message
Your account has expired. Please see your system administrator. |
Password last set:
HKEY_LOCAL_MACHINE\SAM\SAM\Domains\Account\Users\000003EF\F:18-length:8bytes Stored NT time format |
Password expires:
Obtained from: \Security Settings\Account Policies\Password Policy\Maximum password age
Logon Message
Your password has expired and must be changed.
A dialog appears to change the password, once completed(if allowed) logon commences. Builtin Administrator and Guest accounts never expire. |
Password changeable:
Obtained from: \Security Settings\Account Policies\Password Policy\Minimum password age = X days (0 = immediate) |
Password required:
C:\>net user %username% /passwordreq:yes/y/no/n
Unsure what this option is for. (If set to no, then the password for the user must be blank or the user will not be able to logon - an error as if incorrect username or password was attempted.) |
User may change password:
C:\>net user %username% /passwordchg:yes/y/no/n
This can deny a logon if the password expires, error:
Change Password
You do not have permission to change your password. |
Workstations allowed:
C:\>net user foo /workstations:%computername%
C:\>net user foo /workstations:%computername1%;%computername2%,%computername3%
C:\>net user foo /workstations: (all)
Maximum of 8 workstations allowed of >=1 & <=15 character in length
Logon Message
Your account is configured to prevent you from using this computer. Please try another computer. |
Logon script:
have to be >=0 and <=259 C:\>net user %username% /scriptpath:%folder\script.bat/cmd%
Script paths are made relative to this folder: C:\WINNT\System32\repl\import\scripts\ |
User profile:
have to be >=0 and <=259CMD/260GUI C:\>net user %username% /profilepath:%C:\folder or \\machine\folder%
This option is for roaming profiles only! Does not check if the machine name length <=15
By default user profiles determined here: \HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\ProfileList\
REG_SZ:AllUsersProfile = The name of the folder for profile shared stuff (All Users)
REG_SZ:DefaultUserProfile = The name of the "template" profile folder used for newly logged on users (Default User)
REG_EXPAND_SZ:ProfilesDirectory = Where the profiles and the above folders are stored (%SystemDrive%\Documents and Settings)
Each user that has a profile stored will have a subkey within this key in the form \%SID-RID%\
REG_EXPAND_SZ:ProfileImagePath = Location of the users profile. - This not set by the net command!
This can be edited to point to different profiles.
Profiles can either be Local or Roaming. Local are stored in a fixed location and are normally used by standalone machines with a couple of users. Roaming copies a profile from a different location to the local ProfilesDirectory. At logoff this is copied back. Roaming profiles are normally used on domains whereby a user may logon to different machines and keep the same profile.
User profiles are stored in a folder called X, where X follows this order if existing folders already exist:
%username%
%username%.%machinename%
%username%.%machinename%.XXX - where XXX is >=000 and <=999. The system scans up decimally for the first available number. If all these are taken this error shows at logon: User Environment
Windows cannot find the local profile and is logging you on with a temporary profile. Changes you make to this profile will be lost when you log off. Temporary folders follow this order, if existing folders already exist:
TEMP
TEMP.%machinename%
TEMP.%machinename%.XXX - where XXX is >=000 and <=999, the system scans up decimally for the first available number
If all these are take this error shows at logon: User Environment
Windows cannot create a temporary profile directory. Contact your network administrator.
DETAIL - The system cannot find the file specified. Next dialog is very similar: Windows cannot log you on because the profile cannot be loaded. Contact your network administrator. The user is returned to the logon screen. If an adminstrative level account, they are logged on under the default profile for the system. This situation is not likely to occur however. |
Home directory:
C:\>net user %username% /homedir:c:\foo2
Have to be >=0 and <=259CMD/247GUI
GUI can alternatively map a logical drive letter to a remote share >=0 and <=259 \\%machinename%\%sharename% |
Last logon:
HKEY_LOCAL_MACHINE\SAM\SAM\Domains\Account\Users\%userno%\F:offset8/length8 stored NT time format. |
Logon hours allowed:
C:\>net user %username% /times:all
Sunday = su, sunday
Monday = m, monday
Tuesday = t, tuesday
Wednesday = w, wednesday
Thursday = th, thursday
Friday = f, friday
Saturday = s, sa, saturday
/times:%day%,%time%-%time%;%day%,%time%-%time% - eg: s,9am-5pm;su,9am-12pm or m-f,9am-1pm;m-f,2pm-5p
/times:%day%-%day%,%time%-%time% - eg: m-f,9am-5pm
If logon is attempted outside of allowed logon times: Logon Message
Your account has time restrictions that prevent you from logging on at this time. Please try again later.
3 bytes are assigned for each day of the week:
|01,02,03,04,05,06,07,08,09,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24
|FF,FF,FF|FF,FF,FF|FF,FF,FF|FF,FF,FF|FF,FF,FF|FF,FF,FF|FF,FF,FF|00,01,00
| Sunday | Monday |Tuesday |Wednesda|Thursday| Friday |Saturday|Unknown
Add for combinations:
FF,FF,FF = All times
01,00,00 = 12am-01am (midnight)
02,00,00 = 01am-02am
04,00,00 = 02am-03am
08,00,00 = 03am-04am
10,00,00 = 04am-05am
20,00,00 = 05am-06am
40,00,00 = 06am-07am (morning)
80,00,00 = 07am-08am
00,01,00 = 08am-09am
00,02,00 = 09am-10am
00,04,00 = 10am-11am
00,08,00 = 11am-12pm (noon) |
00,10,00 = 12pm-01pm (noon)
00,20,00 = 01pm-02pm
00,40,00 = 02pm-03pm
00,80,00 = 03pm-04pm
00,00,01 = 04pm-05pm
00,00,02 = 05pm-06pm (evening)
00,00,04 = 06pm-07pm
00,00,08 = 07pm-08pm
00,00,10 = 08pm-09pm
00,00,20 = 09pm-10pm
00,00,40 = 10pm-11pm
00,00,80 = 11pm-12am (midnight)
00,00,00 = Not this day | |
 |
| regedit.exe -> \HKEY_LOCAL_MACHINE\SAM\SAM\Domains\Account\Users\%RID%\F (fixed length, 80)
explorer.exe -> \%windir%\system32\config\SAM
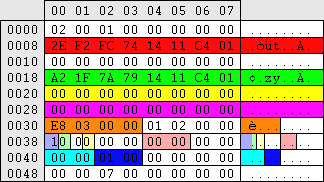
 Password never expire - 0=secpoltime 2=never Password never expire - 0=secpoltime 2=never
For some unknown reason this value is set to 4 on a lockout and 0 on unlocking. If the password is set never to expire the option to force the user to change their password on next logon is greyed out.
2/3/6/7/A/B/E/F=Password never expires (2=GUI setting)
0/2/8/A=logonokay
1/3/5/7/9/B/D/F=Logon Message
The system can not log you on due to the following error:
The account used is a server trust account. Use your global user account or local user account to access this server.
Please try again or consult your system administrator.
4/6/C/E=logonokay - reset to X-4 though. |
 Last logon - stored NT time format, nulls if never logged on Last logon - stored NT time format, nulls if never logged on
 Password last set - stored NT time format, nulls if not changed Password last set - stored NT time format, nulls if not changed
 Account expires - stored NT time format, nulls if set not to expire Account expires - stored NT time format, nulls if set not to expire
 Last incorrect password - stored NT time format, nulls if not Last incorrect password - stored NT time format, nulls if not
 User Number - stored in reverse hex User Number - stored in reverse hex
 Unsure - 0/2/6/8/A/C/E=pwd/username invalid Unsure - 0/2/6/8/A/C/E=pwd/username invalid
1/3/4=logonokay
5/7/D/F=Logon Message
The system can not log you on due to the following error:
The account used is an interdomain trust account. Use your global user account or local user account to access this server.
Please try again or consult your system administrator.
9/B=Logon Message
The system can not log you on due to the following error:
The account used is a computer account. Use your global user account or local user account to access this server.
Please try again or consult your system administrator.
 Account active - 0=active 1=not active. Account active - 0=active 1=not active.
Password required - 0=yes 4=no
0/2/4/6/8/A/C/E=logonokay - 1/2/5/7/9/B/D/F=accountdisabled/inactive
 Country code - stored in reverse hex Country code - stored in reverse hex
 Invalid pwd count - stored in reverse hex, reset after a correct logon Invalid pwd count - stored in reverse hex, reset after a correct logon
 No. of logons - stored in reverse hex, gets stuck at FF,FF No. of logons - stored in reverse hex, gets stuck at FF,FF |
 |
| regedit.exe -> \HKEY_LOCAL_MACHINE\SAM\SAM\Domains\Account\Users\%RID%\V (variable length, 424+)
explorer.exe -> \%windir%\system32\config\SAM
In this anontation the 1st and 3rd section are shown first because they relate to each other, refer to the hex offset on the left.
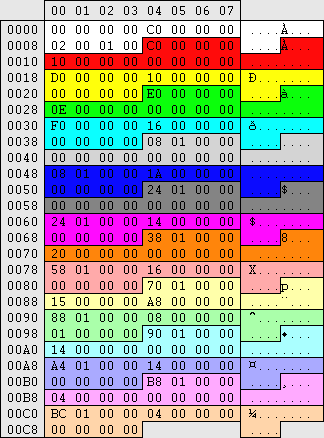 |
The first 12 bytes of the value are unknown, probably section headers
The first 4 bytes of each entry refer to the location of the entry relative to offset:CC Stored in reverse hex
The second 4 bytes refer to the entry length. Space allocated is rounded up to nearest multiple of 4 bytes, ignore the surplus data. Stored in reverse hex
The third 4 bytes are unknown
 Username Username
 Fullname Fullname
 Comment Comment
 User comment User comment
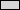 Unknown entry Unknown entry
 Homedir Homedir
 Homedirconnect Homedirconnect
 Scriptpath Scriptpath |
 Profilepath Profilepath
 Workstations Workstations
 Hours allowed Hours allowed
 Unknown entry Unknown entry
 LM password hash LM password hash
 NT password hash NT password hash
 Unknown entry Unknown entry
 Unknown entry Unknown entry | | |
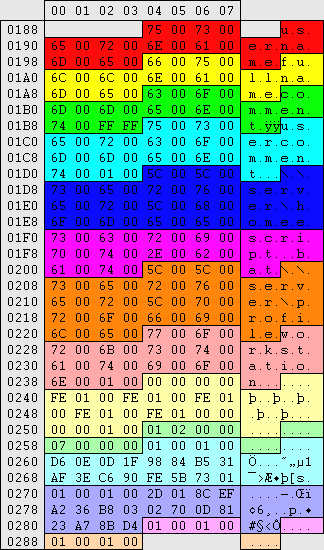 |
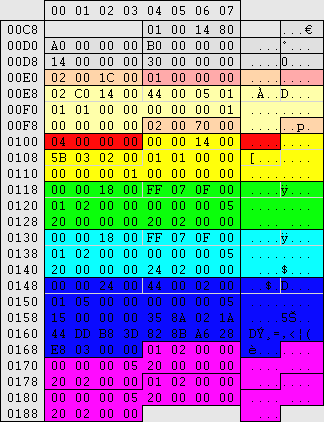 |
This is the middle section of the V value. The first 52 bytes are unknown
 No. of permissions (example:4) No. of permissions (example:4)
 Permission: Everyone Permission: Everyone
 Permission: Administrators Permission: Administrators
 Permission: Account Operators Permission: Account Operators
 Permission: User in question Permission: User in question
 2x Administrators group SID (unknown reason) 2x Administrators group SID (unknown reason)
The 14, 18, 24 (convert to decimal) in the first block of 4 bytes of the user/group permission are believed to state the entry length.
The second 4 byte block holds the user/group permissions. If these settings follow similar storage methods to security settings then each nibble holds 8 combinations, additions of 1, 2, 4 & 8. Not all these options are known.
5B,03,02 = Everyone
44,00,02 = User in question
FF,07,0F = Account Operators & Administrators = full control?
00,00,00 = No permissions
5B,01,00 = List user details
FF,01,00 = Change user settings
FF,01,01 = Delete user
CMD: System error 5 has occurred.
Access is denied.
MSC: Local Users and Groups
The following error occurred while attempting to read user/group properties: Access is denied.
The full user/group sid is stated in the last section |
 |
| By default new users are added to the Users group. There are 6 built-in localgroups in 2K: Administrators, Backup Operators, Guests, Power Users, Replicator & Users. XP added Network Configuration Operators, Remote Desktop Users & HelpServicesGroup. They are listed here: \HKEY_LOCAL_MACHINE\SAM\SAM\Domains\Builtin\Aliases\Names\%groupname% where a subkey's value points to: HKEY_LOCAL_MACHINE\SAM\SAM\Domains\Builtin\Aliases\00000XXX\C which holds details about the group. Not all details are known at this point, however the group name, description/comment and groups members are stored here.
Alias name C:\>net localgroup %groupname% /add - can be >=1 and <=256CMD/254GUI only the first 25 characters are displayed at CMD. Some problems are encounter with longer groups names. Group names can be renamed to 255 characters via GUI, however it does error with: Local Users and Groups
The following error occurred while attempting to rename the group %groupname%:
One or more input parameters are invalid. However the group name will be renamed. On attempting to access the group similar errors occur and on attempting to delete the group, this explanation is given: An invalid Active Directory pathname was passed. Strange since AD is not installed. At CMD any groupname >25 cannot be deleted: The user or group account specified cannot be found.
More help is available by typing NET HELPMSG 3963. Adding users to a 254 length groups seems to trigger network activity, the user is added and can be removed via GUI though. CMD however can handle adding/deleting user to 255/256 length group names, if deletion is attempted in GUI the following error occurs: Local User and Groups
One or more errors occurred while recording group membership changes for user %username%.
Comment/Description C:\>net localgroup %groupname% /comment:"%comments%" >=0 and <=256GUI/2,133CMD which is basically limited by CMD's 2,170 buffer input handling. GUI can render such a comment and rename, but only to a shorter length.
There is also another record stored here: \HKEY_LOCAL_MACHINE\SAM\SAM\Domains\Builtin\Aliases\Members\%dec_SID%\%hex_RID%\ In 2K the default value can be view correctly in regedt32 by Displaying Binary Data. This value simply lists the groups in hex that each respective user is a member of. Local Groups are for workstations, Global Groups are for servers. Custom groups are added here: \HKEY_LOCAL_MACHINE\SAM\SAM\Domains\Account\Aliases\Names\%groupname%\ and follow a similar pattern.
 |
| regedit.exe -> \HKEY_LOCAL_MACHINE\SAM\SAM\Domains\Account\Aliases\%RID%\C (variable length) (custom groups)
regedit.exe -> \HKEY_LOCAL_MACHINE\SAM\SAM\Domains\Builtin\Aliases\00000220\C (variable length) (builtin groups)
explorer.exe -> \%windir%\system32\config\SAM
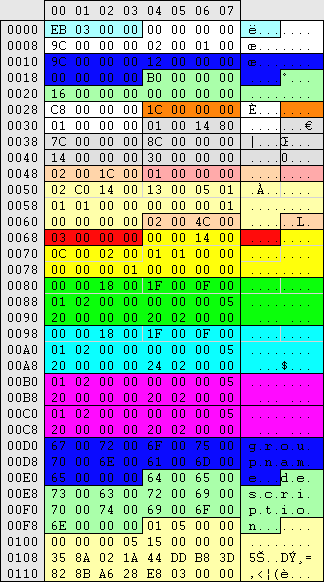 |
Group key offsets are relative from 34
 The group(user) number The group(user) number
 Group name Group name
 Group description Group description
 Length of user entires (reverse hex) Length of user entires (reverse hex)
 Number of users (reverse hex) Number of users (reverse hex)
 Number of group permissions Number of group permissions
 Permission: Everyone Permission: Everyone
 Permission: Administrators Permission: Administrators
 Permission: Account Operators Permission: Account Operators
 2x Administrators group SID (unknown reason) 2x Administrators group SID (unknown reason)
 Group membership represented by their SID Group membership represented by their SID
Group permissions are similar to user permissions:
0C,00,02 = Everyone
1F,00,0F = Administrators
1F,00,0F = Account Operators
1F,00,0F = Power users
09,00,00 = List group (cmd will list the group on 00 permissions)
0D,00,00 = List group members
0F,00,00 = Add/remove group members (all newly created users are added to the users group)
1F,00,00 = Edit groupname/comment (msc only. 1f,00,01 = for cmd edit) |
The main security settings are configurated with secpol.msc or via "Security Configuration and Analysis" in a MMC. Here you can configure directly or import security templates. You can also use Group Policy or gpedit.msc -> \Local Computer Policy\Computer Configuration\Windows Settings\Security Settings\ - this is the same thing and any settings are stored in the normal database and not the Registry.pol files in C:\WINNT\system32\GroupPolicy\(Machine/User)\ The security settings are stored in a separate database (*.sdb) and then written from there to various parts of the registry. The builtin one is located: C:\WINNT\security\Database\secedit.sdb
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\GPExtensions\{827D319E-6EAC-11D2-A4EA-00C04F79F83A}\
"LastPolicyTime"=dword:XXXXXXXX Where X = the number of minutes since 1st Jan 1980. (12797280 = 12:00AM - 1st May 2004) To save time in calculating this value use ntdate.exe This value is created on first altering security settings after install. It is then updated to the current time, when the security settings are refreshed/written. This will occur when closing a dialog on editing settings or at startup if the time stored is in the future or more than 16 hours behind the current time: Applying security policy... (just before logon) An event; SceCli is logged under the Application Log when this occurs at startup. You can also update via command line with C:\>secedit /refreshpolicy machine_policy /enforce
[System Access] (F0,3F,FE)
secpol.msc -> \Account Policy\Password Policy\ and \Account Policy\Account Lockout Policy\
regedit.exe -> \HKEY_LOCAL_MACHINE\SAM\SAM\Domains\Account\F
explorer.exe -> \%windir%\system32\config\SAM
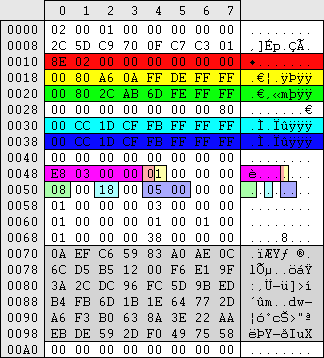 |
 Auto-increment Auto-increment
 Maximum password age (>=0 & <=999)days Maximum password age (>=0 & <=999)days
Reverse bytes, minus from qword:ff + 1 = seconds x 10 million
 Minimum password age (>=0 & <=998)days Minimum password age (>=0 & <=998)days
Reverse bytes, minus from qword:ff + 1 = seconds x 10 million
 Account lockout duration (>=0 & <=99,999)minutes Account lockout duration (>=0 & <=99,999)minutes
Reverse bytes, minus from qword:ff + 1 = seconds x 10 million
 Reset account lockout counter after (>=1 & <=99,999)minutes Reset account lockout counter after (>=1 & <=99,999)minutes
Reverse bytes, minus from qword:ff + 1 = seconds x 10 million
 Next created users RID (mentioned in the users and groups section) Next created users RID (mentioned in the users and groups section)
 Store password using reversible encryption for all user in the domain(enabled=1/disabled=0) Store password using reversible encryption for all user in the domain(enabled=1/disabled=0)
 Password must meet complexity requirements (enabled=1/disabled=0) Password must meet complexity requirements (enabled=1/disabled=0)
 Minimum password length (>=0 & <=14)characters (in hex) Minimum password length (>=0 & <=14)characters (in hex)
 Enforce password history (>=0 & <=24)passwords remembered (in hex) Enforce password history (>=0 & <=24)passwords remembered (in hex)
 Account lockout threshold (>=0 & <=999)attempts (revsere hex) Account lockout threshold (>=0 & <=999)attempts (revsere hex)
 Part of syskey (mentioned in the passwords section) Part of syskey (mentioned in the passwords section) |
 |
| [Event Audit] (26,40,FE)
secpol.msc -> \Local Policies\Audit Policy\@
regedit.exe -> \HKEY_LOCAL_MACHINE\SECURITY\Policy\PolAdtEv\@
explorer.exe -> \%windir%\system32\config\SECURITY

 01 if any audits are enabled, if none: 00 01 if any audits are enabled, if none: 00
 Unsure: 2K=FF0600 XP=000700 - reset to nulls Unsure: 2K=FF0600 XP=000700 - reset to nulls |
 Audit system events Audit system events
 Audit logon events Audit logon events
 Audit object access Audit object access
 Audit privilege use Audit privilege use
 Audit process tracking Audit process tracking
 Audit policy change Audit policy change
 Audit account management Audit account management
 Audit directory service access Audit directory service access
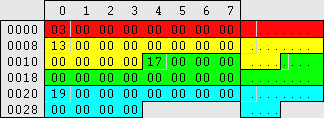
 Audit account logon events Audit account logon events
 No. of policies: 9 - reset if removed No. of policies: 9 - reset if removed
|
The type of policy applied is determined where X = setting, as defined below:
|
[Privilege Rights](00,40,FE)
secpol.msc -> \Local Policies\User Rights Assignment\
explorer.exe -> \%windir%\system32\config\SECURITY
This group of settings are stored in two locations/formats:
regedit.exe -> \HKEY_LOCAL_MACHINE\SECURITY\Policy\Accounts\%SID%\ActSysAc\@
A simple fixed 4 byte hex value - add for combinations
regedit.exe -> \HKEY_LOCAL_MACHINE\SECURITY\Policy\Accounts\%SID%\Privilgs\@
A variable length hex value, of the following layout:
 |
 The first byte states the number of the privilges; followed by 7 nulls The first byte states the number of the privilges; followed by 7 nulls
 Privilege: Shut down the system Privilege: Shut down the system
 Privilege: Bypass traverse checking Privilege: Bypass traverse checking
 Privilege: Remove computer from docking station Privilege: Remove computer from docking station
Each privilege is stored in a 12 byte block. The first byte states the privilege followed by 11 nulls. The privileges do not appear to be stored in any order |
Access this computer from the network ------------------------
Act as part of the operating system --------------------------
Add workstations to domain -----------------------------------
Adjust memory quotas for a process ---------------------------
Allow logon through Terminal Services ------------------------
Back up file and directories ---------------------------------
Bypass traverse checking -------------------------------------
Change the system time ---------------------------------------
Create a pagefile --------------------------------------------
Create a token object ----------------------------------------
Create a global objects --------------------------------------
Create permanent shared objects ------------------------------
Debug programs -----------------------------------------------
Deny access to this computer from the network ----------------
Deny logon as a batch job ------------------------------------
Deny logon as a service --------------------------------------
Deny logon locally -------------------------------------------
Deny logon through Terminal Services -------------------------
Enable computer and user accounts to be trusted for delegation
Force shutdown from a remote system --------------------------
Generate security audits -------------------------------------
Impersonate a client after authentication --------------------
Increase quotas ----------------------------------------------
Increase scheduling priority ---------------------------------
Load and unload device drivers -------------------------------
Lock pages in memory -----------------------------------------
Log on as a batch job ----------------------------------------
Log on as a service ------------------------------------------
Log on locally -----------------------------------------------
Manage auditing and security log -----------------------------
Modify firmware environment values ---------------------------
Perform volume maintenance tasks -----------------------------
Profile single process ---------------------------------------
Profile system performance -----------------------------------
Remove computer from docking station -------------------------
Replace a process level token --------------------------------
Restore files and directories --------------------------------
Shut down the system -----------------------------------------
Synchronize directory service data ---------------------------
Take ownership of file or other objects ---------------------- | |
senetworklogonright -------------
setcbprivilege ------------------
semachineaccountprivilege -------
seincreasequotaprivilege --------
seremoteinteractivelogonright ---
sebackupprivilege ---------------
sechangenotifyprivilege ---------
sesystemtimeprivilege -----------
secreatepagefileprivilege -------
secreatetokenprivilege ----------
secreateglobalprivilege ---------
secreatepermanentprivilege ------
sedebugprivilege ----------------
sedenynetworklogonright ---------
sedenybatchlogonright -----------
sedenyservicelogonright ---------
sedenyinteractivelogonright -----
sedenyremoteinteractivelogonright
seenabledelegationprivilege -----
seremoteshutdownprivilege -------
seauditprivilege ----------------
seimpersonateprivilege ----------
seincreasequotaprivilege --------
seincreasebasepriorityprivilege -
seloaddriverprivilege -----------
selockmemoryprivilege -----------
sebatchlogonright ---------------
seservicelogonright -------------
seinteractivelogonright ---------
sesecurityprivilege -------------
sesystemenvironmentprivilege ----
semanagevolumeprivilege ---------
seprofilesingleprocessprivilege -
sesystemprofileprivilege --------
seundockprivilege ---------------
seassignprimarytokenprivilege ---
serestoreprivilege --------------
seshutdownprivilege -------------
sesyncagentprivilege ------------
setakeownershipprivilege -------- | |
ActSysAc
Privilgs
Privilgs
Privilgs
ActSysAc
Privilgs
Privilgs
Privilgs
Privilgs
Privilgs
Privilgs
Privilgs
Privilgs
Actsysac
Actsysac
Actsysac
Actsysac
ActSysAc
Privilgs
Privilgs
Privilgs
Privilgs
Privilgs
Privilgs
Privilgs
Privilgs
ActSysAc
ActSysAc
ActSysAc
Privilgs
Privilgs
Privilgs
Privilgs
Privilgs
Privilgs
Privilgs
Privilgs
Privilgs
Privilgs
Privilgs | |
02,00,00,00
07
06
05
00,04,00,00
11
17
0C
0F
02
1E
10
14
80,00,00,00
00,01,00,00
00,02,00,00
40,00,00,00
00,08,00,00
1B
18
15
1D
05
0E
0A
04
04,00,00,00
10,00,00,00
01,00,00,00
08
16
1C
0D
0B
19
03
12
13
1A
09 | |
2p,xp
2p,xp
2p,xp
---xp
---xp
2p,xp
2p,xp
2p,xp
2p,xp
2p,xp
2p,xp
2p,xp
2p,xp
2p,xp
2p,xp
2p,xp
2p,xp
---xp
2p,xp
2p,xp
2p,xp
2p,xp
2p---
2p,xp
2p,xp
2p,xp
2p,xp
2p,xp
2p,xp
2p,xp
2p,xp
---xp
2p,xp
2p,xp
2p,xp
2p,xp
2p,xp
2p,xp
2p,xp
2p,xp | |
 |
| [Registry Values](2C,40,FE)
secpol.msc -> \Local Policies\Security Options\
regedit.exe -> Various locations
explorer.exe -> \%windir%\system32\config\SAM|SOFTWARE|SYSTEM
Additional restrictions for anonymous connections
None. Rely on default permissions = 0
Do not allow enumeration of SAM accounts and shares = 1
No access without explicit anonymous permissions = 2
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa\"restrictanonymous"=dword:0000000X
Allow Server Operators to schedule tasks (Domain Controllers Only)
Enabled = 1 or Disabled = 0
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa\"submitcontrol"=dword:0000000X
Allow system to be shutdown without having to log on
Enabled = 1 or Disabled = 0
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\"ShutdownWithoutLogon"="X"
Allowed to eject removable NTFS media
Administrators = 0
Administrators and Power Users = 1
Administrators and Interactive Users = 2
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\"allocatedasd"="0"
Amount of idle time required before disconnecting session (>=0 & <=99999)minutes (0 = Do not disconnect clients)
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\lanmanserver\parameters\"autodisconnect"=dword:000XXXXX
Audit the access of global system objects
Enabled = 1 or Disabled = 0
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa\"auditbaseobjects"=dword:0000000X
Audit use of Backup and Restore privilege
Enabled = 1 or Disabled = 0
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa\"fullprivilegeauditing"=hex:0X
Automatically log off user when logon time expires(local)
Enabled = 1 or Disabled = 0
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\lanmanserver\parameters\"enableforcedlogoff"=dword:0000000X
Clear virtual memory pagefile when system shuts down
Enabled = 1 or Disabled = 0
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management\"ClearPageFileAtShutdown"=dword:0000000X
Digitally sign client communication (always)
Enabled = 1 or Disabled = 0
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\lanmanworkstation\parameters\"requiresecuritysignature"=dword:0000000X
Digitally sign client communication (when possible)
Enabled = 1 or Disabled = 0
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\lanmanworkstation\parameters\"enablesecuritysignature"=dword:0000000X
Digitally sign server communication (always)
Enabled = 1 or Disabled = 0
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\lanmanserver\parameters\"requiresecuritysignature"=dword:0000000X
Digitally sign server communication (when possible)
Enabled = 1 or Disabled = 0
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\lanmanserver\parameters\"enablesecuritysignature"=dword:0000000X
Disable CTRL+ALT+DEL requirement for logon
Enabled = 1 or Disabled = 0
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system\"disablecad"=dword:0000000X
Do not display last username in logon screen
Enabled = 1 or Disabled = 0
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system\"dontdisplaylastusername"=dword:0000000X
LAN Manager Authentication Level
Send LM & NTLM responses = 0
Send LM & NTLM - user NTLMv2 session security if negotiated = 1
Send NTLM response only = 2
Send NTLMv2 response only = 3
Send NTLMv2 response only\refuse LM = 4
Send NTLMv2 response only\refuse LM & NTLM = 5
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa\"lmcompatibilitylevel"=dword:0000000X
Message title for user attempting to log on
(>=1 & <=16,383)characters | - bug(?) dialog = 30,000, if over 16,383 characters removes all/most security values within the key
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system\"legalnoticetext"="X"
Message title for users attempting to log on
(>=1 & <=16,383)characters | - bug(?) dialog = 30,000, if over 16,383 characters removes all/most security values within the key
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system\"legalnoticecaption"="X"
Number of previous logons to cache (in case domain controller is not available)
(>=1 & <=50) logons (0 = Do not cache logons)
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\"cachedlogonscount"="X"
Prevent system maintenance of computer account password
Enabled = 1 or Disabled = 0
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Netlogon\Parameters\"DisablePasswordChange"=dword:0000000X
Prevent users from installing printer drivers
Enabled = 1 or Disabled = 0
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Print\Providers\LanMan Print Services\servers\"addprinterdrivers"=dword:0000000X
Prompt user to change password before expiration
(>=0 & <=999)days
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\"passwordexpirywarning"=dword:00000XXX
Recovery Console: Allow automatic administrative logon
Enabled = 1 or Disabled = 0
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Setup\RecoveryConsole\"SecurityLevel"=dword:0000000X
Recovery Console: Allow floppy copy and access to all drives and all folders
Enabled = 1 or Disabled = 0
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Setup\RecoveryConsole\"SetCommand"=dword:0000000X
Rename administrator account
(>=1 & <=20)characters | - bug(?) dialog = 30,000 (cannot be any existing group/user names)
HKEY_LOCAL_MACHINE\SAM\SAM\Domains\Account\Users\000001F4\V ("towards the end")
HKEY_LOCAL_MACHINE\SAM\SAM\Domains\Account\Users\Names\%username%
Rename guest account
(>=1 & <=20)characters | - bug(?) dialog = 30,000 (cannot be any existing group/user names)
HKEY_LOCAL_MACHINE\SAM\SAM\Domains\Account\Users\000001F5\V ("towards the end")
HKEY_LOCAL_MACHINE\SAM\SAM\Domains\Account\Users\Names\%username%
Restrict CD-ROM access to locally logged-on user only
Enabled = 1 or Disabled = 0
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\"allocatecdroms"="X"
Restrict floppy access to locally logged-on user only
Enabled = 1 or Disabled = 0
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\"allocatefloppies"="X"
Secure channel: Digitally encrypt or sign secure channel data (always)
Enabled = 1 or Disabled = 0
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Netlogon\Parameters\"requiresignorseal"=dword:0000000X
Secure channel: Digitally encrypt secure channel data (when possible)
Enabled = 1 or Disabled = 0
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Netlogon\Parameters\"sealsecurechannel"=dword:0000000X
Secure channel: Digitally sign secure channel data (when possible)
Enabled = 1 or Disabled = 0
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Netlogon\Parameters\"signsecurechannel"=dword:0000000X
Secure channel: Require strong (Windows 2000 or later) session key
Enabled = 1 or Disabled = 0
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Netlogon\Parameters\"requirestrongkey"=dword:0000000X
Send unencrypted password to connect to third-party SMB servers
Enabled = 1 or Disabled = 0
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\lanmanworkstation\parameters\"enableplaintextpassword"=dword:0000000X
Shutdown system immediately if unable to log security audits
Enabled = 1 or Disabled = 0
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa\"crashonauditfail"=dword:0000000X
Smart card removal behaviour
No Action = 0
Lock Workstation = 1
Force Logoff = 2
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\"scremoveoption"="X"
Strengthen default permissions of global system objects (e.g. Symbolic Links)
Enabled = 1 or Disabled = 0
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\"ProtectionMode"=dword:0000000X
Unsigned driver installation behaviour
Silently succeed = 0
Warn but allow installation = 1
Do not allow installation = 2
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Driver Signing\"Policy"=hex:0X
Unsigned non-driver installation behavior
Silently succeed = 0
Warn but allow installation = 1
Do not allow installation = 2
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Non-Driver Signing\"Policy"=hex:0X
 |
| secpol.msc -> \Event Log\Settings for Event Logs\
regedit.exe -> HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Eventlog\(Application/Security/System)\
explorer.exe -> \%windir%\system32\config\SYSTEM
[Application Log](24,40,FE) | [Security Log](22,40,FE) | [System Log](20,40,FE)
Maximum log size for (Application/Security/System) Log (>=64 & <=4,194,240)KBytes | 64byte Increment
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\EventLog\(Application/Security/System)\"MaxSize"=dword:XXXXXXXX
Restrict Guest access to (Application/Security/System) Log
Enabled = 1 or Disabled = 0
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Eventlog\(Application/Security/System)\"RestrictGuestAccess"=dword:0000000X
Retain (Application/Security/System) Log
(>=1 & <= 365)days (stored in seconds, only visable if Retention method is by days)
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Eventlog\(Application/Security/System)\"Retention"=dword:0XXXXXXX
Retention method for (Application/Security/System) Log
Overwrite events by days = As above (days * seconds)
Overwrite events as needed = 0
Do no overwrite events (clean log manually) = FFFFFFFF
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Eventlog\(Application/Security/System)\"Retention"=dword:XXXXXXXX
[Event Audit](26,40,FE)
Shutdown system when security audit becomes full
Enabled = 1 or Disabled = 0
HKEY_LOCAL_MACHINE\SECURITY\Policy\PolAdtFL\@=hex(0):0X,00
 |
| [Group Membership](08,40,FE)
secpol.msc -> \Restricted Groups\
regedit.exe -> Not defined here
explorer.exe -> \%windir%\security\Database\secedit.sdb
Listed are the groups: Administrators, Backup Operators, Guests, Power Users, Replicator & Users.
In the members tab users can be defined in the security database to belong to the respective group. When the security policy is applied the registry group membership is matched with the list in the database, hence if a new administrator is added to the machine, but not listed in the security policy, it will be removed on policy application. This setting is only defined in the security database.
In the Member of tab is the text: The groups to which this group belongs should not be modified. Unsure, this setting doesn't "seem" to work since local/custom groups cannot be added to local groups - DC only?
 |
| [Service General Setting](2E,40,FE)
secpol.msc -> \System Services\
regedit.exe -> HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\%Various%
explorer.exe -> \%windir%\system32\config\SYSTEM
Service startup mode (FYI: 0=boot, 1=system, 2=automatic 3=manual, 4=disabled, 5+=unknown)
2 = Automatic
3 = Manual
4 = Disabled
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\%service%\"Start"=dword:0000000X
Service Security
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\%service%\Security\"Security"=hex:01,00,14,80...
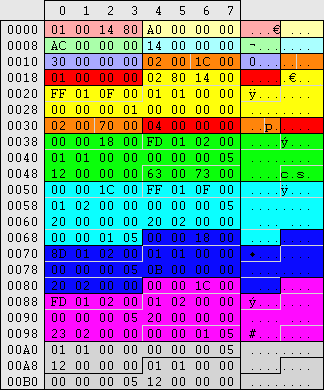 |
 Constant for all service security values Constant for all service security values
 Length from start to the first SYSTEM SID at the end Length from start to the first SYSTEM SID at the end
 Length from start to the second SYSTEM SID at the end Length from start to the second SYSTEM SID at the end
 Header length Header length
 Length from beginning to start of permissions Length from beginning to start of permissions
 The section(audit/permission) prefix, the second two bytes state the section length The section(audit/permission) prefix, the second two bytes state the section length
 The number of users/groups within the section The number of users/groups within the section
 Audit: Everyone Audit: Everyone
 Permission: SYSTEM Permission: SYSTEM
 Permission: Administrators Permission: Administrators
 Permission: Authenticated Users Permission: Authenticated Users
 Permission: Power Users Permission: Power Users
 SYSTEM SID - unsure of purpose SYSTEM SID - unsure of purpose
The audit and permission entries hold several sections of data.
The third byte in the first dword holds the entry length.
The second dword holds the permission/audit setting: (add for combinations)
FF,01,0F,00 = Full Control
01,00,00,00 = Query template
02,00,00,00 = Change template
04,00,00,00 = Query status
08,00,00,00 = Enumerate dependents
10,00,00,00 = Start
20,00,00,00 = Stop
40,00,00,00 = Pause and continue
80,00,00,00 = Interrogate
00,01,00,00 = User-defined control
00,00,01,00 = Delete
00,00,02,00 = Read permissions
00,00,04,00 = Change permissions
00,00,08,00 = Take ownership
The section after the permissions is the respective user/group SID number.
After this is a dword - unsure of purpose. |
 |
| [Registry Keys] 14,40,FE
secpol.msc -> \Registry\
regedit.exe -> Stored in SK values that are not actually viewable via regedit/regedt32 -> Security -> Permissions...
explorer.exe -> \%windir%\system32\config\(SAM/SECURITY/SOFTWARE/SYSTEM) and %USERPROFILE%\NTUSER.DAT
This part is explained in the registry structure section.
 |
| [File Security] 18,40,FE
secpol.msc -> \File System\
regedit.exe -> Not stored here
explorer.exe -> Differs from NT4(NTFSv1.2) and 2k/XP(NTFSv3.0/3.1)
This is should possibly be expanded into a whole different article on NTFS, however here are afew brief details. In NT4 the privilege is stored within each respective $MFT entry. In 2K/XP each $MFT entry has a numbered permission assigned to it - all the permissions are stored in the $Secure file in numbered permission blocks. This allows multiple files to point to the same permission block, saving space. Storage format is very similar to other permissions with the first dword specifying the length, followed by the privilege and then the SID. If you are using XP home, use FaJo XP File Security Extension to view the settings in normal mode.
FF,01,1F,00 = Full Control
20,00,10,00 = Traverse Folder / Execute File
01,00,10,00 = List Folder / Read Data
80,00,10,00 = Read Attributes
08,00,10,00 = Read Extended Attributes
02,00,10,00 = Create Files / Write Data
04,00,10,00 = Create Folders / Append Data
00,01,10,00 = Write Attributes
10,00,10,00 = Write Extended Attributes
40,00,10,00 = Delete Subfolders and Files
00,00,11,00 = Delete
00,00,12,00 = Read Permissions
00,00,14,00 = Change Permissions
00,00,18,00 = Take Ownership
 |
|
 |
| Apart from the audit log(.Evt), EFS keys, file security, group policies(.pol), and security databases(.sdb), all security settings are stored in the registry. In the second table the filenames are with respect to the path and filenames in the first table. A&P is the number of unique audit and permission entries.
|
|
|
|
C:\WINNT\system32\config\default ------------------------------------------------------------------
C:\WINNT\system32\config\SAM ----------------------------------------------------------------------
C:\WINNT\system32\config\SECURITY -----------------------------------------------------------------
C:\WINNT\system32\config\software -----------------------------------------------------------------
C:\WINNT\system32\config\system -------------------------------------------------------------------
C:\WINNT\system32\config\userdiff -----------------------------------------------------------------
C:\Documents and Settings\%username%\NTUSER.DAT ---------------------------------------------------
C:\Documents and Settings\%username%\Local Settings\Application Data\Microsoft\Windows\UsrClass.dat
C:\Documents and Settings\Default User\NTUSER.DAT ------------------------------------------------- | |
System profile ---------------
Users and Groups -------------
Security Settings ------------
User/OS software settings ----
Hardware settings & services -
Unsure, not loaded either? ---
Individual user settings -----
Empty and Unused? ------------
Default settings for new users | |
- 122,880
-- 20,480
-- 20,480
6,119,424
2,428,928
- 139,264
- 225,280
--- 8,192
- 118,784 | |
|
|
|
|
|
|
|
|
|
|
AppEvents, Console, Control Panel, Environment, Identities, Keyboard Layout,
Software, UNICODE Program Groups | |
|
|
|
|
|
|
|
|
|
| HKEY_LOCAL_MACHINE\SECURITY\ | |
|
|
|
|
|
HKEY_LOCAL_MACHINE\SOFTWARE\
| |
|
Classes, Clients, INTEL, Microsoft, ODBC, Policies, Program Groups, Secure,
Voice, Windows 3.1 Migration Status | |
|
|
|
| HKEY_LOCAL_MACHINE\SYSTEM\ | |
|
| ControlSet001, ControlSet002, MountedDevices, Select, Setup | |
|
|
|
|
|
| 61 numbers ranging 1137 to 2138 | |
|
|
|
HKEY_CURRENT_USER\
HKEY_USERS\SID-RID\ | |
|
AppEvents, Console, Control Panel, Environment, Identities, Keyboard Layout,
Printers, RemoteAccess, Software, UNICODE Program Groups | |
|
|
|
| HKEY_USERS\SID-RID_Classes\ | |
|
|
|
|
|
|
|
AppEvents, Console, Control Panel, Environment, Identities, Keyboard Layout,
Software, UNICODE Program Groups | |
|
 |
| This image is a scale diagram of a SAM registry hive: (1 horizontal pixel = 32 bytes)

 Header Header
 Surplus space - filled with nulls Surplus space - filled with nulls
 hbin entries - repeated every 4096(8192/12288) from offset 4096 hbin entries - repeated every 4096(8192/12288) from offset 4096
 Registry keys, values, data and permissions etc Registry keys, values, data and permissions etc
At the end of the entries a dword states the length inclusively to the end of the file followed by FF,FF,FF,FF
 Surplus space - nulls or junk Surplus space - nulls or junk |
The header section is 512 bytes, because the middle section does not appear to be used, this is absent from the diagram below - note offsets:
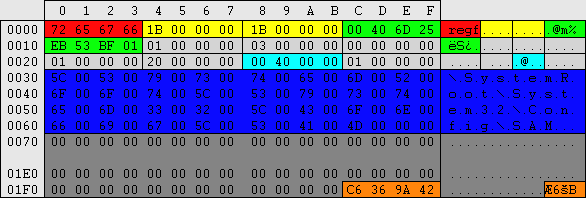 |
 regf; a constant identifier regf; a constant identifier
 Twin increment for adding/removing data in memory; Twin increment for adding/removing data in memory;
appears to add by 2, the left before the right
 Last disk write - shutdown, logoff and other times; Last disk write - shutdown, logoff and other times;
stored NT time format
 Constants, unsure of; the 2nd one is set to 05000000 Constants, unsure of; the 2nd one is set to 05000000
in default, software, system & userdiff in XP. The
2nd from last is 32 bytes - possible hbin reference?
 Length of data section to the end of the last hbin Length of data section to the end of the last hbin
 The filename and path, counting backwards The filename and path, counting backwards
 Surplus space - nulls or junk Surplus space - nulls or junk
 Dword XOR checksum of the first 508 bytes Dword XOR checksum of the first 508 bytes |
|
|
 Path Path | |
default
NTUSER.DAT
SAM
SECURITY
software
SYSTEM
userdiff
UsrClass.dat | |
stemRoot\System32\Config\DEFAULT
ettings\Administrator\ntuser.dat
\SystemRoot\System32\Config\SAM
emRoot\System32\Config\SECURITY
emRoot\System32\Config\SOFTWARE
SYSTEM
1\WINNT\SYSTEM32\CONFIG\userdiff
\Microsoft\Windows\UsrClass.dat | | |
The path in the NTUSER.DAT in the default profile directory is set to nulls.
emRoot/stemRoot is SystemRoot without the %
1\WINNT is probably:
\Device\HarddiskVolume1\ |
You could use
calc.exe to XOR;
scientific view
and switch to Bin |
Instead you could use xorcheck.exe to save time in calculating the checksum
C:\>Usage: xorcheck
Point to a 508 byte file that contains the first 508 bytes of the hive, reverse the output bytes |
 |
| The hbin entry:
 |
 hbin; a constant identifier hbin; a constant identifier
 Offset of entry with respect to offset 1000 Offset of entry with respect to offset 1000
 Either the length of entry or offset to next entry Either the length of entry or offset to next entry
relative to this one. Normally 1000/4069 but can
switch between 2000 and 3000 part way through
 Surplus space - nulls or junk Surplus space - nulls or junk
 2K Constant? - mostly junk or nulls in XP 2K Constant? - mostly junk or nulls in XP |
 |
| The registry appears to be made up of 7 different types of entries:
All offsets are relative to 1000, xx denotes no constant identifier
01. nk = (sub)keys (links to the following 4 types)
02. lf/lh = Subkey list
03. xx = Value list (links to type no. 6)
04. sk = Permissions
05. xx = Class information (regedt32 input on key creation)
06. vk = Value (links to type no. 7 though data can be within the value)
07. xx = Data
 |
| The nk entry:
 Entry length, 100000000 - reversed bytes Entry length, 100000000 - reversed bytes
 nk; a constant identifier nk; a constant identifier
 Keytype: 2C = Rootkey. 20 = Subkey Keytype: 2C = Rootkey. 20 = Subkey
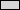 Constants - unsure of purpose Constants - unsure of purpose
 NT date format, set at key creation and modified the key is renamed or if NT date format, set at key creation and modified the key is renamed or if
values within are added or changed. Does not change for any subkey changes
 Parent key offset, what the root key points to is unclear Parent key offset, what the root key points to is unclear
 Number of subkeys, unsure of maximum, if none; filled with 00,00,00,00 Number of subkeys, unsure of maximum, if none; filled with 00,00,00,00
 Subkey list(lf) offset, if none; filled with FF,FF,FF,FF Subkey list(lf) offset, if none; filled with FF,FF,FF,FF
 Number of values, unsure of maximum, if none; filled with 00,00,00,00 Number of values, unsure of maximum, if none; filled with 00,00,00,00
 Values list offset, if none; filled with FF,FF,FF,FF Values list offset, if none; filled with FF,FF,FF,FF
 Audit and permissions(sk) offset Audit and permissions(sk) offset
 Class entry offset, if none; filled with FF,FF,FF,FF Class entry offset, if none; filled with FF,FF,FF,FF
 The maximum subkey's name length x 2, if none; filled with 00,00,00,00. The maximum subkey's name length x 2, if none; filled with 00,00,00,00.
Possibly a memory feature: in the SYSTEM file, the maximum key length stated is
22 -> 17 which = CurrentControlSet, which is not stored in the actual file.
 The maximum subkey's class size, if none; filled with 00,00,00,00 The maximum subkey's class size, if none; filled with 00,00,00,00
 The maximum value's name length, if none; filled with 00,00,00,00 The maximum value's name length, if none; filled with 00,00,00,00
 The maximum value's data size, if none; filled with 00,00,00,00 The maximum value's data size, if none; filled with 00,00,00,00
 Surplus space - nulls or junk Surplus space - nulls or junk
 Keyname length - NB: If the length is set to 1 more than the "real" length and Keyname length - NB: If the length is set to 1 more than the "real" length and
a null suffixed to the end of the name, the key will be handled similarly to
these subkeys: SAC, SAI, XATM etc in HKEY_LOCAL_MACHINE\SECURITY\Policy\Secrets\
(FYI: XATM is thought to stand for: XA Transaction Manager, unsure of purpose.
The SA keys are used for scheduled tasks) regedit.exe -> Error Opening Key
Cannot open %keyname%: Error while opening key. regedt32.exe -> Greyed out;
Security -> Permissions... -> Unable to display security information.
 Class length (max = d0,07 -> 07,d0 = 2,000(unicode stored, hence 1000 char) Class length (max = d0,07 -> 07,d0 = 2,000(unicode stored, hence 1000 char)
 Keyname; stored in ASCII format. Ignore surplus bytes, length is stated Keyname; stored in ASCII format. Ignore surplus bytes, length is stated |
 |
| Subkey list:
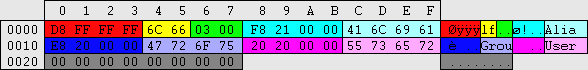 |
 Entry length, 100000000 - reversed bytes Entry length, 100000000 - reversed bytes
 lk; a constant identifier lk; a constant identifier
 No. of subkeys (can be obtained from the key though) No. of subkeys (can be obtained from the key though)
   Offsets to subkeys, followed by the first Offsets to subkeys, followed by the first
   four characters of the subkey name four characters of the subkey name
 Surplus space - nulls or junk Surplus space - nulls or junk |
XP uses a checksum instead of the 1st four characters on the following 4 files: default, software, SYSTEM & userdiff
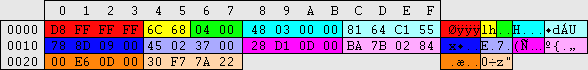 |
As above, with this difference:
 lh; a constant identifier (for checksumed lists) lh; a constant identifier (for checksumed lists)
The subkeys are: Control, Enum, Hardware Profiles & Services respectfully. |
Calculating the checksum: Control = 43,6F,6E,74,72,6F,6C -> 43,4F,4E,54,52,4F,4C (CONTROL)
Use calc.exe, view = Scientific, length = Dword
43 + 4F = 92 + (43 x 24) = 9FE
9FE + 4E = A4C + (9FE x 24) = 17204
17204 + 54 = 17258 + (17204 x 24) = 357AE8
357AE8 + 52 = 357B3A + (357AE8 x 24) = 7BAC3DA
7BAC3DA + 4F = 7BAC429 + (7BAC3DA x 24) = 1DFE4ED1
1DFE4ED1 + 4C = 1DFE4F1D + (1DFE4ED1 x 24) = 55C16481 -> 55,C1,64,81 -> 81,64,C1,55
Values list:
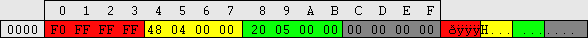 |
 Entry length, 100000000 - reversed bytes Entry length, 100000000 - reversed bytes
  Offsets to values Offsets to values
 Surplus space - nulls or junk Surplus space - nulls or junk |
 |
| Audit and permissions:
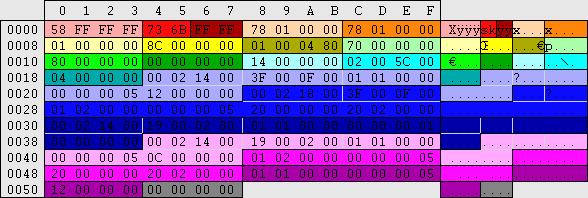
 Entry length, 100000000 - reversed bytes Entry length, 100000000 - reversed bytes
 sk; constant identifier sk; constant identifier
 *mostly* FF,FF/00,00 though other values noted - unsure of purpose *mostly* FF,FF/00,00 though other values noted - unsure of purpose
 Next sk entry in the "sequence" - see right -> Next sk entry in the "sequence" - see right ->
 Previous sk entry in the "sequence" see right -> Previous sk entry in the "sequence" see right ->
 Constant 01,00,00,00 - unsure of purpose Constant 01,00,00,00 - unsure of purpose
 Length of entry(not surplus) from offset 18 (which is right after this dword) Length of entry(not surplus) from offset 18 (which is right after this dword)
All offset here after are with respect of offset 18
 Unsure, however the lower nibble of the last byte determines propagation -> Unsure, however the lower nibble of the last byte determines propagation ->
Allow inheritable permissions from parent to propagate to this object ->
Allow inheritable auditing entries from parent to propagate to this object ->
 Owner of item; offset to Owner of item; offset to
 SYSTEM SID; offset to SYSTEM SID; offset to
 Audit entries; offset to - 00,00,00,00 if none Audit entries; offset to - 00,00,00,00 if none
 Permission entries; offset to - unusual to have none, but if so: 00,00,00,00 Permission entries; offset to - unusual to have none, but if so: 00,00,00,00
Registry Editor could not accomplish the requested operation - but still loads
with the key greyed out, permissions can be added.
 Audit/permissions - the 1st/2nd bytes are 02,00 - constants. Audit/permissions - the 1st/2nd bytes are 02,00 - constants.
3rd/4th = length of audit section entry (if none: 02,00,08,00 - this and next)
 Number of audit/permission entries (if none: 00,00,00,00) Number of audit/permission entries (if none: 00,00,00,00)
    There are some differences in the first 2 bytes between audit(left) and permission(right) entries. There are some differences in the first 2 bytes between audit(left) and permission(right) entries.
Audit:
1st byte = 02 - constant?
2nd byte, lower nibble denotes the type of audit:
| |
|
|
Allow
Deny
Allow & deny - if both settings
are identical, else two entries
are created | | | 2nd byte, upper nibble denotes the scope of the audit/permission.
See table on the right ->
3rd(& possibly 4th) byte is the length of this audit/permission entry
 Owner of item, SID of Owner of item, SID of
 SYSTEM SID - unsure of purpose SYSTEM SID - unsure of purpose
 Surplus space - nulls or junk Surplus space - nulls or junk |
|
|
|
|
|
|
|
|
|
|
11,78
3A,B0
10,78
2F,88
36,60 | |
|
2F,88
10,78
36,60
3A,B0
11,78 | |
| |
If 1 sk, both point to itself
If 2 sk, both point to each other |
Next: 1078,1178,3AB0,3660,2F88 ->
Prev: 1078,2F88,3660,3AB0,1178 <-
|
|
|
|
|
Inherit both
Inherit audits only
Inherit permissions only
No inherits | | |
When applying permissions or audits to a parent key, propagation will check there-and-then and update any subkeys flagged |
|
|
|
01,00,00,00
02,00,00,00
04,00,00,00
08,00,00,00
10,00,00,00
20,00,00,00
00,00,01,00
00,00,04,00
00,00,08,00
00,00,02,00
3F,00,0F,00 | |
Query Value
Set Value
Create Subkey
Enumerate Subkeys
Notify
Create Link
Delete
Write DAC
Write Owner
Read Control
Full Control | |
Permissions:
1st byte: allow=00/deny=01
2nd byte, lower nibble = 0
2nd byte, upper nibble denotes the scope of permission:
|
|
|
|
|
This key and subkeys
Apply these permissions to objects and/or
containers within this container only | |
|
|
Subkeys only
Apply these permissions to objects and/or
containers within this container only | |
Deny entries take priority over Allow entries, which can cause unintended effects due to group membership. Deny permissions entries are ordered before allow entries - a possible exit on 1st deny, access on 1st allow? |
 |
| Class:
This is a kinda hidden attribute of registry keys, since it is not displayed in regedt32/regedit gui. The only way other than programatically or debug to view the class information is to "Save Subtree As..." in regedt32 and check the Class Name: for values other than Mainly this feature is used in the CLSID and Interface subkeys of software\Classes - however others were noted on keys to do with: Internet Explorer, TCP service, OS/2 and syskey(mentioned in the passwords section)
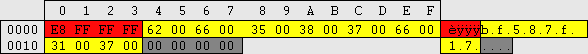 |
 Entry length, 100000000 - reversed bytes Entry length, 100000000 - reversed bytes
 Class data in unicode Class data in unicode
 Surplus space - nulls or junk Surplus space - nulls or junk |
 |
| Values:
There appears to be two types of values, values that contain data and values that point to data. The name is optional for both types, but if a value is not asigned a name, regedit renders it (Default); regedt32
Named value that contains data:
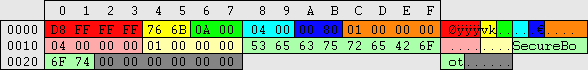
Named value that links to data:
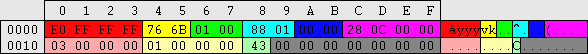
Unnamed value that links to data:
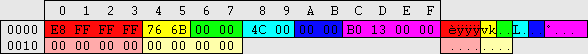
Unnamed value that contains data in the form of its value type:
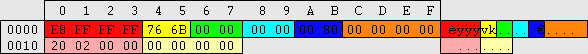 |
 Entry length, 100000000 - reversed bytes Entry length, 100000000 - reversed bytes
 vk; constant identifier vk; constant identifier
 Unsure of purpose Unsure of purpose
 Length of value's data Length of value's data
 00,80 = contains data. 00,00 = linked to data 00,80 = contains data. 00,00 = linked to data
 Data contain within the value Data contain within the value
 Offset to linked data Offset to linked data
 Value type - see table below Value type - see table below
 00 = no named value. 01 = named value 00 = no named value. 01 = named value
 Value's name Value's name
 Surplus space - nulls or junk Surplus space - nulls or junk
|
|
|
|
|
|
|
REG_NONE ---------------------
REG_SZ -----------------------
REG_EXPAND_SZ ----------------
REG_BINARY -------------------
REG_DWORD --------------------
REG_DWORD_LITTLE_ENDIAN ------
REG_LINK ---------------------
REG_MULTI_SZ -----------------
REG_RESOURCE_LIST ------------
REG_FULL_SOURCE_DESCRIPTOR ---
REG_RESOURCE_REQUIREMENTS_LIST
REG_QWORD -------------------- | |
-------------
REG_SZ ------
REG_EXPAND_SZ
REG_BINARY --
REG_DWORD ---
-------------
-------------
REG_MULTI_SZ
-------------
-------------
-------------
------------- | |
-------
String
-------
Binary
DWORD -
-------
-------
-------
-------
-------
-------
------- | | |
Regedit can only handle REG_SZ and REG_EXPAND_SZ values of data size 3F,FF or less, anything above and the value disappears - regedt32 can handle up to 30,000. Regedit and regedt32 can both handle REG_BINARY values of data size 3F,FF or less. DWORD value have a data size of 4 bytes. Regedit can only handle REG_MULTI_SZ values of data size 3F,FE - this is because of the null included at the end - regedt32 can handle up to 7,FF,FC which is 4 bytes short of 1/2 a megabyte - anything over errors: Registry Editor could not accomplish the requested operation.
 |
| Data:
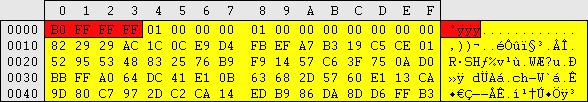 |
 Entry length, 100000000 - reversed bytes Entry length, 100000000 - reversed bytes
 Data Data |
Examples of SAM and SECURITY registry files
The SAM file appears to be "fairly" secure - however if physical access to the machine is possible it is not so secure; Microsoft have admitted this. The SAM file is locked. It is not possible to delete/copy/move/rename it within windows via explorer. Access to RAM is also restricted if not in the administrator group. Disk hexeditors can only be used within windows if logged in with administrative privileges, else direct disk access is denied. Administrative privileges are needed to defragment a volume so the sam file may need assembling if direct access of the disk is used. If the machine can be (re)booted from a different device eg, floppy or the hard disk removed and/or copied, there are possibilities.
Passwords are not stored in the sam file, password hashes are. This means that the password has to be hashed and then compared - passwords cannot be directly extracted. Once the hashes have been obtained, they can be tested with dictionary files or for all possible combinations. The time this takes depends on the complexity and length of the password for the account. To prevent simple dumping of the hashes from the registry, syskey.exe - SAM Lock Tool was introduced into service pack >=3 for NT4. Enabling syskey is a one way process, once enabled it cannot be disabled - according to Microsoft. Service pack 3 did not automatically enable syskey, the administrator had to set it. In 2K+ it is enabled by default. Syskey adds an extra level of encryption to the hashes and makes the hashes unique to the system and the usernumber.
Syskey can work in one of three different ways - with some trickery all three can be deployed at the same time ;-)
|
|
|
|
|
|
Store Startup Key Locally
Password Startup
Store Startup Key on Floppy Disk | |
Stores a key as part of the operating system, and no interaction is required during system start.
Requires a password to be entered during system start.
Requires a floppy disk to be inserted during system start. | |
A non-determining record of which option is enabled is stored here:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa\"SecureBoot"=dword:0000000X
If option 2 or 3 is chosen a prompt will appear at startup, just as the mouse appears. Either the correct floppy disk needs to be in the drive or the correct password entered to proceed to the regular login. If option 3 is chosen a 16 byte file will be saved to floppy disk by the name of "startkey.key" By default option 1 is selected in 2K/XP and this is believed to be the most commonly used option.
Although the hashes are encrypted, the correct hashes can be obtained with pwdump via lsass.exe if logged on in the Administrators group of the system in question. There are other programs that use similar/same techniques to Todd Sabin's that can retrive the hashes.
Local privilege escalation: If access to a account in Administrators groups is not available, raise the user level of an existing one. There maybe many to chose from, but assume that there is not. One account that is probably always available is the builtin Guest. The computer needs to be booted from a different device, either from a FD/CD (BIOS may need altering/cracking) or remove the disk and temporarily connect to another machine to make the changes. More stealthy is to dd/image the target disk and carry out the procedure on a similar machine elsewhere.
Boot from Petter Nordahl-Hagen's boot disk: (windows users may want to read up on the commands cp and mount)
| 01. |
(optional) Make a copy of the SAM and SECURITY files, or note all changes made. This is in case of any errors. |
| 02. |
(optional) Make a copy of the event log files: Application(appevent.evt) Security(secevent.evt) & System(sysevent.evt) or note the audit settings and the security policy refresh time and temporaraly switch off auditing. This is to prevent Windows based auditing. |
| 03. |
Check the username for user 000001F5. If (not a *BLANK* password) or (an unknown one) set one. |
| 04. |
Activate the Guest or user account (see users and groups section) |
| 05. |
Change the permission level to Administrator (see users and groups section) |
| 06. |
Increase the number of Administrators (see users and groups section) |
| 07. |
Check security policies, can the user logon? - change if not (see users and groups section) |
| 08. |
Bootup and login as Guest/user and dump the correct hashes. Reboot and restore all files to their original state. Test hashes on a different machine. |
Exporting the syskey: The sys part of syskey does not refer to the hardware, thus it can be moved to another system. This method also requires booting from a different device, but actual booting of the target disk is not needed, which makes this method passive. Bootup and copy the following information:
01. \SAM\SAM\Domains\Account\F (Data of) - The 48 bytes at the end minus 8 bytes. (see the security settings section)
02. \SAM\SAM\Domains\Account\Users\000001F4\V (Data of) - 2 x 16 bytes at the end minus 8 bytes. (see the passwords section)
03. \SECURITY\Policy\PolSecretEncryptionKey\@ (Data of) - The last 64 bytes, basically all of this value.
04. \SYSTEM\ControlSet001\Control\Lsa\Data\ (Class of) - 8 bytes of hex in text (see the registry structure section)
05. \SYSTEM\ControlSet001\Control\Lsa\GBG\ (Class of) - As above
06. \SYSTEM\ControlSet001\Control\Lsa\JD\ (Class of) - As above
07. \SYSTEM\ControlSet001\Control\Lsa\Skew1\ (Class of) - As above
On a second system create or use an account with a usernumber different from the one you are importing, raise the privileges of this user to Administrator if not already. Set this account's password to blank - not via GUI but in the registry at HKEY_LOCAL_MACHINE\SAM\SAM\Domains\Account\Users\XXXXXXXX where X is the user's account number. This is a similar process to setting a blank password with Petter Nordahl-Hagen's boot disk or creating a new user without specifing a password. Refer to the Users and Groups section - alter the bytes after data for the logon hours allowed to read: 01,02,00,00,07,00,00,00 , 01,00,01,00 , 01,00,01,00 , 01,00,01,00 , 01,00,01,00 then update the offsets towards the start of the key, add 8 to the offset of the unknown entry for the LM hash, then 4 for the NT, then 4 for the unknown entry, and finally 4 again for the last unknown entry. Reboot for update.
If you do not already have a user of the same user number of the account you are importing either create one by modifying the next user number counter (see users and groups section) or you could edit a dummy user's account, user's number and the group values.
Import the specific data into the host computer. For the F and V values, it maybe quicker to export the existing value, paste in the specific new data and import. Just import PolSecretEncryptionKey striaght as there are no other settings here. For the class data probably quicker to export as reg files, delete the keys, use regedt32 to create new keys with new classes, then import the exported reg files.
Reboot and login as the user with the *blank* password, and dump the correct hashes.
The c:\boot.ini file is very important at the first stages of starting an NT system. It determines the location of the %windir% directory that the system is going to load from. By default Administrators and System have full control and Power Users have "Read & Execute" and Read permissions. File attribute are set to archive, system and hidden. Although most directories have restrictive permissions for users, root folder permissions (see partition properties) are set to Everyone having full control - this permission is not set to be inherited by any objects in the root directory. However the root folder permissions do have an effect on non-read-only files in root even if they are set not to inherit parent permissions. Feature or flaw? All the other files in root are either read-only, locked by the operating system (handles) or non-critical. This does not effect folders. The boot.ini file is not readonly which is strange since the configuration of the file in "System Properties" -> Advanced -> "Startup and Recovery" is not effected by this attribute.
Due to this weakness in NTFS permissions a User can delete the boot.ini file and replace it with their own. This newly created boot.ini would include an option to boot from a different OS bypassing the security model. There are two ways of doing this:
01. Mobile OS
02. Recovery Console
Both have advantages and disadvantages. Read both as I have expanded on a few issues in the latter.
Mobile OS:
On a different system start the 2K setup from floppy disk. When the copying finishes reboot from a floppy/other system and edit these files:
C:\TXTSETUP.SIF -> DefaultPath=\WINNT
C:\$WIN_NT$.~LS\I386\HIVESFT.INF -> DEFAULT_PROFILES_DIR="%SystemDrive%\Documents and Settings"
Point them to different locations so they do not interfer with the target system setup. Continue with the setup. On completion disable the Recycle Bin & hibernation feature, delete unneeded files and shrink the pagefile in order to reduce the total size of the system. Add any usefull programs also, but avoid/delete the "Program Files" directory as you will not have permission to overwrite on the target system. Also visit this page: http://support.microsoft.com/default.aspx?scid=kb;[LN];Q314082 - it states this only applies to XP, but basically they just updated KBQ271965 slightly which applied to 2K and then deleted the orginal one. *frowns at MS* On the target system open and resave the current boot.ini elsewhere, replace with one that will also point to your setup. Copy the mobile setup over, you will probably need to run attrib -r /s /d on the folder if copied from CD. Reboot and select your setup. Press F8 and boot into safe mode, this is very important as it allows the keyboard and mouse to be detected properly. Reboot in normal mode for full access, some drivers may need to be added for fully system functionality. Hyperthetically the new %SystemRoot% could hold a "ntldr friendly" coded program instead.
Recovery Console:
Normally one would boot from CD and select the Recovery Console option in the setup, however you can install it on your computer by running: D:\i386\winnt32.exe /cmdcons This takes up about 5.58MB which can be compressed down to 3.86MB - If you know the hardware configuration of the target computer you can reduce this even further by deleting most of the drivers and editing the txtsetup.sif file - example:
[SCSI.Load]
atapi = atapi.sys,4
[InputDevicesSupport.Load]
[BusExtenders.Load]
pciide = pciide.sys
mountmgr = mountmgr.sys
ftdisk = ftdisk.sys
partmgr = partmgr.sys
fdc = fdc.sys
[BootBusExtenders.Load]
pci = pci.sys
acpi = acpi.sys
Also most of the files are aleady present in the host system, so you can copy them to the cmdcons directory - either way the files will fit onto a couple of floppy disks - quite doable. Use the method detailed above to get the files onto the system. The boot.ini file should look something like this:
[boot loader]
timeout=5
default=multi(0)disk(0)rdisk(0)partition(1)\WINNT
[operating systems]
multi(0)disk(0)rdisk(0)partition(1)\WINNT="Microsoft Windows 2000 Professional1" /fastdetect
multi(0)disk(0)rdisk(0)partition(2)\WINNT="Microsoft Windows 2000 Professional2" /fastdetect
multi(0)disk(0)rdisk(0)partition(3)\WINNT="Microsoft Windows 2000 Professional3" /fastdetect
C:\CMDCONS\BOOTSECT.DAT="Microsoft Windows 2000 Recovery Console" /cmdcons
Notice there are three different partitions specified for Windows 2000, this is incase there is more than one partition present - stops you from getting locked out if the system is not in the 1st partition.
Delete the boot.ini file. Replace it with your own. copy the cmdcons directory and the cmldr file into root.
When you load the Recovery Console you have to enter the Administrator's password in order to get access to the system, however there is a weakness in this process. In order to find the system(s) which the user can logon to it scans the directories in root and looks within these for a subfolder of system32 and within this, subfolders of config and drivers. This is logical, the %windir% directory can vary - in NT4 the setup includes the option to change the path, and in 2000 and XP you can use an unattend or modify the TXTSETUP.SIF file to point to a different path. The system32 directory is constant as are the config and drivers directories, both of which hold critical files for an NT boot. If the sam, security and system files are present in the config directory, the user will be prompted for the builtin administrators password, once authenticated they will only have access to files with the SID that they logged on with. This would not be a problem, since the SID of the target machine could be found by browsing to C:\Documents and Settings\foo\Application Data\Microsoft\Crypto\RSA\ where foo is their username. Within this folder is a folder with the machine's SID number followed by the user RID number, on a separate system this could be inserted, either with Sysinternals NewSID program or manually in the registry and a known password set for the administrators account. The slight flaw is that if the sam, security and system files are not present, a user does not have to logon and gets access to everything.
Simply create 2 folders named config and drivers in the C:\cmdcons\system32 directory. You will be give a choice as to which system you would like to logon as - select the C:\cmdcons one.
The BOOTSECT.DAT file has 3 parameters that are critical for startup and will vary depending on the partition size and its position on the disk.
1. Sectors per cluster, located at offset D. The Microsoft Knowledge Base has this table:
|
|
|
|
512MB or less
513MB to 1024MB(1GB)
1025MB to 2048MB(2GB)
2049MB and larger | |
512 bytes
1024 bytes (1KB)
2048 bytes (2KB)
4096 bytes (4KB) | |
|
Check the capacity of the C drive in properties. - this is the total size of the partition. In this case it was: 39,941,955,584 bytes.
2. Hidden sectors, located at offset 1C. This is the number of sectors from the beginning of the drive to the start of the partition. If the system is setup from a blank disk with default settings this will be 63 sectors (32,256 bytes). If there are multiple partitions and the partition in question is not the first then this value will be much larger. Multiple partition could exist for the following reasons: hardware ultilites, imaged system, other operating systems and hardware level system hibernation storage etc - however they will *probably* be located at the end of the drive which will not effect the hidden sectors value.
To check; run devmgmt.msc -> expand "Disk drives" and check the model name/number. In this case it was: WDC WD400BB-75FRA0. Lookup the drive on the manufactures website and get the technical specifications for the drive. This Western Digital drive is 40,020,664,320 bytes in size. If the partition is 39,941,955,584 bytes and 32,256 bytes are set aside at the beginning, that leaves 78,676,480 bytes or 75 megabytes; which indicates that another partition is possibly present. This maynot be case however - I do not have a free disk at present to check the setups default allocation style for large disks, this maybe surplus space that the largest possible partition for the drive cannot address, if it is not then 153,665 will probably be needed to be added to the hidden sectors. This could be a show stopper.
3. Logical cluster no. of the $MFT, located at offset 38. Like the sectors per cluster, this varies in a similar fashion. Due to the boot loader I was using I could not narrow this down to exact MB, hence this table is alittle approximate:
|
|
|
|
514,079
1,044,224
2,088,448
4,192,964
8,385,928
16,771,856 | |
263,208,448
534,642,688
1,069,285,376
2,146,797,568
4,293,595,136
8,587,190,272 | |
|
This is not a problem, since the partition in question is large. However if the partition was orginally formatted with fat32, ie an upgrade then these figures are likely to be incorrect as the conversion of the file tables would *probably* leave the existing data where is it and simply create a new file table in some free space further on in the disk.
Once all the files are in place, reboot the machine -> select the Recovery Console -> "Logon" to C:\CMDCONS -> cd to: C:\WINNT\system32\config\ -> rename the sam file to something else -> exit to reboot -> select logon to local machine in the drop down list -> logon as administrator with a blank password.
To patch againt both methods, Administrators could either:
1. Run attrib -r -a -s -h c:\boot.ini twice, first with - then with +; at \\machinename... - this is a very simple fix.
2. Uncheck the "Delete subfolders and Files" and/or "Create Files/Write Data", "Create Folders/Append Data" permissions on the partition.
This security issue does not effect default setups. Third-party programs, started as a service must be present - however this is not uncommon. The issue arises when the ImagePath in \HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\%servicename%\ points to an executable in the program files directory and the path does not have "" around it. Due to the space in C:\Program Files\ the system tries to run C:\Program.exe first and pass Files\... to the executable as a parameter. If this is the case the real service will not be started. Since users can save files to the root directory and services tend to run at system level this could be quite serious. Microsoft "appears" to be aware of this - at logon/desktop this dialog (explorer.exe \dialog\20\1033\) will appear if there is a file entitled program.x (where x can be anything/anylength - or just "program") in the root directory.
File Name Warning
There is a file or folder on your computer called "C:\Program.exe"
which could cause certain applications to not function correctly.
Renaming it to "C:\Program1.exe" would solve this problem. Would
you like to rename it now?
[ ] Don't perform this check at startup [Rename] [Ignore]
If the box is checked, this registry key is created:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\DontShowMeThisDialogAgain]
"RogueProgramName"="no" (data = anything else switches the warning back on)
This is poor coding in Microsoft's part since services tend to load before this warning is shown. Additionally it should scan the root directory for all folders with spaces in and then for all executable files in root with names of the first part of the folder name with a space in eg: C:\foo.exe will execute instead of C:\foo bar\...
This would also cover some non-english OS versions:
(N.B: this table is incomplete and unverified)
|
|
|
Danish
Dutch/English/French
Finnish/Swedish
German
Italian
Norwegian
Portuguese
Spanish | |
C:\PROGRAMMER\
C:\Program Files\
C:\PROGRAM\
C:\Programme\
C:\PROGRAMMI\
C:\PROGRAMFILER\
C:\PROGRAMAS\
C:\ARCHIVOS DE PROGRAMA\ | |
As you can see, some versions are not at risk. To patch against this, Administrators could either:
1. Uncheck the "Create Files/Write Data" permission on the partition.
2. Surround the insecure ImagePath in "".
If the SAM file is deleted, Windows onboot will simply recreate one - 1 Administrator and 1 Guest with blank passwords, Guest disabled. If this procedure is attempted on XP the following error occurs on bootup: lsass.exe - System Error
Security Accounts Manager initialization failed because of the following error: A device attached to the system is not functioning. Error Status: 0xC0000001. Please click OK to shutdown this system and reboot into Safe Mode, check the event log for more detailed information. Rebooting into safe mode produces the same error, however if you boot from Petter Nordahl-Hagen's boot disk and change this registry value: \HKEY_LOCAL_MACHINE\SYSTEM\Setup\SystemSetupInProgress to 0x1 - reboot - it will error with: Windows Message
The system is not fully installed. Please run setup again. Click OK to reboot and change the value back to 0x0 and reboot again. A new SAM file will of been created.
The lsass process caches the plain text password of the user logged on in its memory space. This exists while in logged on, logged off, standby and hibernate modes. As soon as a different person logs on, the previous cache is wiped/overwritten. Since lsass loads fairly low down the chances of this appearing in pagefile.sys are small and since you need administrator level+ privileges to access lsass memory space it is reasonably secure locally, however if the machine is on a network this could be a problem, example:
C:\>pslist lsass \\192.168.0.49 -u administrator -p pass (get pid of lsass)
C:\>psexec.exe \\192.168.0.49 -c pmdump.exe 220 foo.dat (220 = lsass pid at time of this test)
C:\>move \\192.168.0.49\admin$\system32\foo.dat c:
Open and search for: 0E003F000001080000000000 where 3F is a wildcard (Winhex). The logon/domain password is located 20 bytes after this. An Administrator could find out users passwords instantly, bypassing part of the security model. Also in network environments, Administrators may tend to set the same Administrator password across many client machines and not update it. Thus reasonably effort could be made to test the hashes of the administrator account, knowing that if successfull, access to other accounts is possible.
Wordlists are very effective on weak passwords. For example a 2.59mb file contains 235,007 words and common passwords, all these can be checked in seconds. LC5 can run hybrid tests, using the wordlist, combinations of numbers and special characters are appended to the end of each tested word, this is also very effective. Interestingly LC4 added the "letters like numbers" feature mentioned in my previous article under the option "Common letter substitutions". A quick look at the lc4.exe file at offset:727E4 shows: "A4@ 8B8 E3 H# I1! L1 O0 S$5 T+7" I have added spaces to divide each section. This will find passwords like p455w0rd very quickly.
Passwords that are "random" can take more time. There are two different 16 byte hashes generated from the password. the LAN Manager (LANMan or LM) hash and the NT (New Technology(?)) hash. The LM hash is DES (Data Encryption Standard) is used for backwards compatibility network access with default 9x/NT4 systems. The NT hash is MD4 (Message Digest Version 4) and is used to logon locally/locked screen or more securely via networks.
The method of LM hashing is not that secure. LM hashing cannot be applied to password of length 15 or more, if such a password is set the LM hash will be AAD3B435B51404EEAAD3B435B51404EE, which is a blank password.
Letters are converted into uppercase, reducing letter combinations by 26, example:
| PASSWORD: |
password: |
LMHash = E52CAC67419A9A224A3B108F3FA6CB6D
NTHash = 7B592E4F8178B4C75788531B2E747687 |
LMHash = E52CAC67419A9A224A3B108F3FA6CB6D
NTHash = 8846F7EAEE8FB117AD06BDD830B7586C |
The password is then split into two sets of 7 and hashed _independently_ of each other. This means only combinations of upto 7 character in length have to be tested, even for a 14 character length password, example:
| 12345671234567: |
LMHash = 0182BD0BD4444BF8 0182BD0BD4444BF8
NTHash = 2D1B7B6660258186 BAA95B6F64003667 |
Programs test the DES hash first, then test NT hash for the correct case. The latter part takes very little time. Due to this weakness service pack 2 for Windows 2000 updated the samsrv.dll to allow the option of not storing a LM hash. Simply add a subkey to Lsa named NoLMHash - located here: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa\NoLMHash reboot and change passwords for update. XP updated this a little to be a value instead: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa\"nolmhash"=dword:00000001 no reboot is required, but passwords must be changed for update. This option is GUI configurable via secpol.msc \Security Settings\Local Policies\Security Options\Network Security: Do not store LAN Manager hash value on next password change.
The same passwords create the same hashes, thus a database could be formed of all possible hashes. The advantages of this would be pretty much instant passwords every time using minimal processor power, the main disadvantage is space. Such a database would be huge, however some research has been done into reducing the size: http://www.antsight.com/zsl/rainbowcrack/ though this still takes some time and does not find all passwords. What would be great is the aforementioned database. The last time the database size was calculated, a custom file system was designed. This file system was made up of blocks of 16 offsets, each one refering to each hex byte 0 - F. The program would know where in the block each nibble was as the offsets would be the same length and would take the offset matching the hex value in the hash and jump to the next block. This would repeat until jumping to the last block where the password would be written - this design took up far too much space. The answer is much simpler -> don't bother indexing all values!!
So how much space does the raw data take up?
The LMHash is 16 bytes long; since they are hashed independently only 8 bytes are used per hash. The password will be of variable length from 0 to 7 characters long. Standard compression could reduce these sizes by about 20% though this will affect performance.
Permutations to the power of length = combinations:
(hash(8) * combinations)
+ (password length(0-7) * combinations)
= Total size for length |
|
|
|
|
|
|
|
8
234
6,760
193,336
5,483,712
154,457,888
4,324,820,864
120,477,152,640 | |
8
324
12,960
513,216
20,155,392
786,060,288
30,474,952,704
1,175,462,461,440 | |
8
621
47,610
3,613,599
272,005,452
20,332,407,537
4,748,399,175,564
111,695,298,788,835 | |
|
|
124,962,115,442
116 gigabytes | |
1,206,744,156,332
1 terabyte | |
116,464,306,039,226
106 terabytes | | |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
154,457,888
9,653,618
603,351 | |
|
|
|
|
4,324,820,864
270,301,304
16,893,831
1,055,864 | |
|
|
|
|
120,477,152,640
7,529,822,040
470,613,877
29,413,367
1,838,335 | | |
The hash values will not increment sequencially so addressing needs to be done by splitting the files into smaller searchable segments. While you could split into equally sized parts, it is more optimal to split on a nibbles of the password hash, variable for each length. The smaller the files the quicker the search, though creation will take longer. Files will be of variable length within each length so the file sizes are approximate. See left for letters only. Using the smallest file size for each length there will be 69,908 files in total. Each file would be named using this format:
(password length)_(from hex value range)_(to hex value range)
eg: 7_D48E000000000000_D48EFFFFFFFFFFFF
This enables direct opening of files, rather than working out if the filename was greater or lesser than the hash in question.
A database has been created for letters and/or numbers passwords. You can access this database by simply telnetting to: 81.7.44.173 on port 2501 (ip address subject to change) or you can download the GUI client (91,648 bytes) Mirror1 | Mirror2
This configuration will return a password in less than half a second.
|
The diagram to the right shows the last three entries of file 6_0000000000000000_0000FFFFFFFFFFFF - as you can see the data is simply password|hash. A significant improvement would be to remove the section that is referenced in the filename; 0000.
The saving would be: permutations * No. of nibbles used for file division / 2. Where there is an odd number of nibbles used, the data structure can simply be changed to 2xpassword|2xhash respectfully.
The current letters and numbers database is 1,206,744,156,332 bytes.
A saving could be made of 200,356,377,120 bytes.
The new database size would be 1,006,387,779,212 bytes.
With Hitachi/IBM pushing the envelope on drive sizes, a precomputated database of hashes & passwords is starting to look very viable.
N.B: HDD manufactures like to use the conversion of: "1 GB equals one billion bytes" which is of course incorrect. The aforementioned drive is really 465 gigabytes, 677 megabytes & 162 kilobytes |
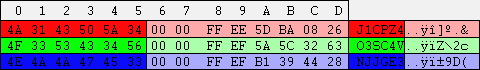
|
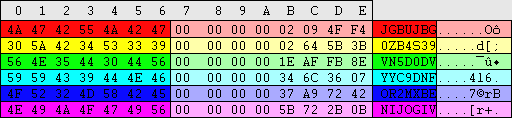
Above is the first 6 entries of 7_0000000000000000_00000FFFFFFFFFFF
As mentioned above we could removed the nibbles mentioned within the
filename, in this case 5, leaving a hash of 11 nibbles.
A more optimal technique of storage would be to just store the first hash
within the file and subsquently store the difference between this and the
following hash. Since the hashes are sorted in order the smallest value
will hashes adjacent relational difference, see right. |
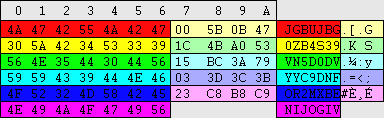
New format 7_0000000000000000_00000FFFFFFFFFFF_0000000002094FF4
01 hash = 0000000002094FF4 (last section of filename)
02 hash = 0000000002094FF4 + 005B0B47 = 0000000002645B3B
03 hash = 0000000002645B3B + 1C4BA053 = 000000001EAFFB8E
04 hash = 000000001EAFFB8E + 15BC3A79 = 00000000346C3607
05 hash = 00000000346C3607 + 033D3C3B = 0000000037A97242
06 hash = 0000000037A97242 + 23C8B8C9 = 000000005B722B0B |
The differences between every hash of that length would need to be calculated prior to converting, if using a fixed width storage of difference. In this case the hash storage has been halfed. Programatically the additions will add very little CPU time during a password lookup. Although the first hash has been appended to the filename, it should really be stored first thing within the file to the keep direct opening of files, since the first hash would be unknown - the layout is easier to understand with it separate. It is worth noting that this technique gets more effective as the number of hashes increases, since the difference between adjacent hashes will decrease.
| A technique that would drastically reduce storage, but add CPU time is to remove blocks of hashes completely. This is a trade-off method. As you can see right there are 9 passwords stored, though only the first and last have hashes assiocated with them. When doing a hash lookup if the hash was between 00000002E359E359 and 000000155B53811D the server would generate hashes for the passwords inbetween to find the correct one. |
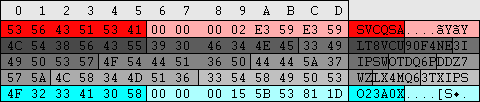 |
To calculate the trade-off you would need to benchmark the server in generating hashes. Using PWSex on an AMD Sempron 2200+ (1,500 MHz) the average speed for checking 7 length alphanumeric LMHashes is over 4,000,000 per second, thus if a trade-off of about 5 seconds was required, only ~4,000 hashes would need to be stored!!
Currently: (78,364,164,096[permutations] x 7[password]) + (78,364,164,096[permutations] x 8[LMHash]) = 1,175,462,461,440 bytes (1 terabyte)
5SecTrade: (78,364,164,096[permutations] x 7[password]) + (~4,000[permutations] x 8[LMHash]) = ~548,549,180,672 bytes (511 gigabytes)
It is worth noting that a trade-off database will have large sections of just letters and numbers, which compresses very well, though this would also add to CPU time during lookup. This technique would most optimal on longer hashing methods like MD5 and SHA1.
This idea could be taken even further in the form of a "zero hash" database. Whereby hashes are not stored at all, only passwords indexed by the hash are. Passwords do not have to be sorted too, since checking random passwords within a certain hash boundary would be no quicker than searching ordered ones - this majourly reduces the database creation time and space required since you would effectively sort at generation.
Eg: LMHash, letters(upper), numbers and special characters has 69 permutations. Assuming for simplicity ~4,000,000 per second for all lengths with a less than 1 second trade for each lookup - remember 2 look ups for each length will need to be done to check all lengths + both halfs.
|
|
|
|
|
|
|
|
|
|
0
69
4,761
328,509
22,667,121
1,564,031,349
107,918,163,081
7,446,353,252,589 | |
0
69
9,522
985,527
90,668,484
7,820,156,745
647,508,978,486
52,124,472,768,123 | |
0
15.87
2,190.06
226,671.21
20,853,751.32
1,798,636,051.35
148,927,065,051.78
11,988,628,736,668.29 | |
0
53.13
7,331.94
758,855.79
69,814,732.68
6,021,520,693.65
498,581,913,434.22
40,135,844,031,454.71 | |
|
0
0
0
0
16
4,096
65,536
16,777,216 | |
|
|
|
|
|
|
|
|
The grey columns indicate the space saving using compression - all other calculations are done without compression in mind. While you could use real splitting, it is simpler to split by nibbles of the hash. This will alter the trade-off time depending on which way you round.
A database for length 1 to 3 does not need to be generated since there is no splitting used. When generating for 4+ the program would run through the combinations sequencely, generating hashes. It would check the hash generated and based on the number of nibbles for that length, append the password to the appropriate file, as mentioned before, no sorting within the file itself needs to take place - eg for 5 length:
AAAAA = A80F6E6A87BA6AC2 -> append password only to file 5_A800000000000000_A80FFFFFFFFFFFFF
BAAAA = 465BEB053958FE47 -> append password only to file 5_4650000000000000_465FFFFFFFFFFFFF
CAAAA = B695FF607DC68979 -> append password only to file 5_B690000000000000_B69FFFFFFFFFFFFF
To prevent the file system becoming a complete mess, some memory or temporary file buffering would be used, as would a post generation defrag to clear up the larger chunks and bring the directory structure together for faster find/load times. Compression could be used at the generation stage - using a buffer as before and compressing in chucks. It is worth noting that this technique is hardly effected (storage wise) by algorithms of a greater bit length since the hash storage is simply, minimally a filename.
 |
| The third way is to test all combinations. The times are the maximum - all combinations up to and including that length. Most of the tests have only been carried out once. A few were double checked, but it was found that the times only varied by seconds, however due to the length of time some of the tests take, some background system processes may slow the process down slightly leeding to a couple of minutes variation. To calculate the number of permutations, do permutations to the power of length, eg: a 4 length, letters only password has 456,976 permutations (26x26x26x26).
When the test is carried out, you have to specify the level of complexity at the beginning. An improvement here would be to test progressively. First test letters only, then test combinations with letters _and_ numbers, as just letters have already been tested. Special characters could also be tested progressively, many people would probably only use one or two special characters. Once letters and numbers have been tested for that length add in each special character individually - then increase the number of special characters to test for the remaining combinations.
(letters) ABC or AaBcCc = ABCDEFGHIJKLMNOPQRSTUVWXYZ (26) or AaBbCcDdEeFfGgHhIiJjKkLlMmNnOoPpQqRrSsTtUuVvWwXxYyZz (52) respectfully
(numbers) 123 = 0123456789 (10)
(special) !@$ = space!"#$%&'()*+,-./:;<=>?@[\]^_`{|}~ (33)
(number) = Number of permutations (x)
In this test only US special characters were used in the special character group.
UK keyboards add 2 extra special characters: £¬
Also of note are the [Alt Gr] key combinations - these are not included.
PWSEx handles all correctly. LC5 does not handle any of these.
The � does not generate a LM hash. LM hashes are generated from uppercase letters.
| |
|
LM |
Case |
Accent |
|
NT |
Case |
Accent |
|
LM |
Case |
Accent |
|
NT |
Case |
Accent |
| � 80/128 |
|
n |
- |
- |
|
n |
- |
- |
|
n |
- |
- |
|
y |
- |
- |
| £ A3/163 |
|
n |
- |
- |
|
n |
- |
- |
|
y |
- |
- |
|
y |
- |
- |
| ¦ A6/166 |
|
n |
- |
- |
|
n |
- |
- |
|
y |
- |
- |
|
y |
- |
- |
| ¬ Ac/172 |
|
n |
- |
- |
|
n |
- |
- |
|
y |
- |
- |
|
y |
- |
- |
| Á C1/193 |
|
n |
n |
n |
|
n |
n |
n |
|
y |
y |
y |
|
y |
y |
y |
| É C9/201 |
|
n |
n |
n |
|
n |
n |
n |
|
y |
y |
y |
|
y |
y |
y |
| Í CD/205 |
|
n |
n |
n |
|
n |
n |
n |
|
y |
y |
y |
|
y |
y |
y |
| Ó D3/211 |
|
n |
n |
n |
|
n |
n |
n |
|
y |
y |
y |
|
y |
y |
y |
| Ú DA/218 |
|
n |
n |
n |
|
n |
n |
n |
|
y |
y |
y |
|
y |
y |
y |
| �� E1/225 |
|
n |
n |
n |
|
n |
n |
n |
|
y |
n |
y |
|
y |
y |
y |
| �� E9/233 |
|
n |
n |
n |
|
n |
n |
n |
|
y |
n |
y |
|
y |
y |
y |
| �� ED/237 |
|
n |
n |
n |
|
n |
n |
n |
|
y |
n |
y |
|
y |
y |
y |
| �� F3/243 |
|
n |
n |
n |
|
n |
n |
n |
|
y |
n |
y |
|
y |
y |
y |
| �� FA/250 |
|
n |
n |
n |
|
n |
n |
n |
|
y |
n |
y |
|
y |
y |
y |
Test OS is Microsoft Windows XP Professional x64 Edition [Version 5.2.3790] (slight performance increase noted over 2K)
Processor is 1 x AMD Athlon FX-53 - Socket 940 (This 64bit processor/OS is backwards compatible with most(?) 32 bit applications)
Motherboard is SK8N from ASUS - Memory is dual-channel Kingston DDR400.
Some overclocking was achieved by changing the FSB frequency. This was different for each program as they became unstable at different speeds. These times maybe increased or decreased in the near future, depending of stability in longer tests. Clock speeds were logged by CPU-Z.
Testing program is LC5 = L0phtCrack (Version 5.02) FSB frequency: 217 - Clock speed: 2603Mhz
01=
02=
03=
04=
05=
06=
07=
08=
09=
10=
11=
12=
13=
14=
15+ |
Testing LM hashes (NT hash verified quickly) |
01=
02=
03=
04=
05=
06=
07=
08=
09=
10=
11=
12=
13=
14=
15+ |
Testing NT hashes only (No LM hash) |
| ABC (26) |
ABC 123 (36) |
ABC 123 !@$ (69) |
AaBbCc (52) |
AaBbCc 123 (62) |
AaBbCc 123 !@$ (95) |
Very short time
Very short time
Very short time
Very short time
01 sec
39 sec
17 min 15 sec
17 min 14 sec
17 min 15 sec
17 min 15 sec
17 min 14 sec
17 min 14 sec
17 min 14 sec
17 min 14 sec
No LM hash |
Very short time
Very short time
Very short time
Very short time
07 sec
04 min 16 sec
02 hrs 34 min 42 sec
02 hrs 34 min 42 sec
02 hrs 34 min 42 sec
02 hrs 34 min 43 sec
02 hrs 34 min 42 sec
02 hrs 34 min 43 sec
02 hrs 34 min 43 sec
02 hrs 34 min 42 sec
No LM hash |
Very short time
Very short time
Very short time
02 sec
02 min 50 sec
03 hrs 16 min 24 sec
Pending... 9.4 days
No LM hash |
Very short time
Very short time
Very short time
05 sec
04 min 33 sec
03 hrs 59 min 21 sec
Pending... 8.6 days
More than 1 PC needed |
Very short time
Very short time
Very short time
10 sec
11 min 02 sec
11 hrs 13 min 41 sec
Pending... 29.0 days
More than 1 PC needed |
Very short time
Very short time
Very short time
57 sec
01 hrs 31 min 05 sec
Pending... 6.0 days
More than 1 PC needed | |
Testing program is PWSEx = Proactive Windows Security Explorer (Version 1.10 / Build 1724) FSB frequency: 215 - Clock speed: 2580Mhz
01=
02=
03=
04=
05=
06=
07=
08=
09=
10=
11=
12=
13=
14=
15+ |
Testing LM hashes (NT hash verified quickly) |
01=
02=
03=
04=
05=
06=
07=
08=
09=
10=
11=
12=
13=
14=
15+ |
Testing NT hashes only (No LM hash) |
| ABC (26) |
ABC 123 (36) |
ABC 123 !@$ (69) |
AaBbCc (52) |
AaBbCc 123 (62) |
AaBbCc 123 !@$ (95) |
Very short time
Very short time
Very short time
Very short time
01 sec
39 sec
18 min 28 sec
18 min 28 sec
18 min 28 sec
18 min 28 sec
18 min 29 sec
18 min 29 sec
18 min 28 sec
18 min 33 sec
No LM hash |
Very short time
Very short time
Very short time
Very short time
07 sec
04 min 33 sec
02 hrs 58 min 48 sec
02 hrs 58 min 47 sec
02 hrs 58 min 48 sec
02 hrs 58 min 48 sec
02 hrs 58 min 47 sec
02 hrs 58 min 48 sec
02 hrs 58 min 50 sec
02 hrs 59 min 42 sec
No LM hash |
Very short time
Very short time
Very short time
03 sec
03 min 02 sec
03 hrs 48 min 49 sec
Pending... 11.2 days
No LM hash |
Very short time
Very short time
Very short time
01 sec
52 sec
44 min 55 sec
39 hrs 14 min 43 sec
More than 1 PC needed |
Very short time
Very short time
Very short time
02 sec
02 min 05 sec
02 hrs 08 min 38 sec
Pending... 5.5 days
More than 1 PC needed |
Very short time
Very short time
Very short time
11 sec
17 min 29 sec
27 hrs 34 min 42 sec
More than 1 PC needed | |
Default security policy setting for maximum password age is 42 days (6 weeks) Now you can see why hashing two sections independently makes slightly longer passwords no more secure, and why disabling the LM hash is a _really_ good idea. Where does your current password/hash fit into and when was the last time you changed it? Remember this is only one standard machine, testing times will fall dramatically on a distributed setup (more than one machine).
Only ASCII characters 1 to 255 maybe used in a password. These characters are looped into the unicode range, eg: 0, 256, 512, 1024... do not produce passwords, while: 1, 257, 513, 1025... all produce the same hashes. The NT hash is unique within this range. The LM hash has some duplicates besides the upper/lower case letters, see right columns. Most/all(?) programs do not test for control and extended characters as the high permutations make testing futile. These characters can be entered via the alt+numpad (alt+fn+numpad on laptops) method.
Total NT permutations: 255
Total LM permutations: 203 |
 129 13F7984C0D47E484 129 13F7984C0D47E484
 154 13F7984C0D47E484 154 13F7984C0D47E484
 69 17306D272A9441BB 69 17306D272A9441BB
 101 17306D272A9441BB 101 17306D272A9441BB
 136 17306D272A9441BB 136 17306D272A9441BB
 137 17306D272A9441BB 137 17306D272A9441BB
 138 17306D272A9441BB 138 17306D272A9441BB
 164 20BDD3E50B0AE760 164 20BDD3E50B0AE760
 165 20BDD3E50B0AE760 165 20BDD3E50B0AE760
 228 2560C3F6D827B66B 228 2560C3F6D827B66B
 229 2560C3F6D827B66B 229 2560C3F6D827B66B
 145 25D8AB4A0659C97A 145 25D8AB4A0659C97A
 146 25D8AB4A0659C97A 146 25D8AB4A0659C97A |
 148 350AACEB37EDB148 148 350AACEB37EDB148
 153 350AACEB37EDB148 153 350AACEB37EDB148
 232 4E007A297C16C370 232 4E007A297C16C370
 237 4E007A297C16C370 237 4E007A297C16C370
 85 613E9293942509F0 85 613E9293942509F0
 117 613E9293942509F0 117 613E9293942509F0
 150 613E9293942509F0 150 613E9293942509F0
 151 613E9293942509F0 151 613E9293942509F0
 163 613E9293942509F0 163 613E9293942509F0
 65 7584248B8D2C9F9E 65 7584248B8D2C9F9E
 97 7584248B8D2C9F9E 97 7584248B8D2C9F9E
 131 7584248B8D2C9F9E 131 7584248B8D2C9F9E
 133 7584248B8D2C9F9E 133 7584248B8D2C9F9E
 160 7584248B8D2C9F9E 160 7584248B8D2C9F9E |
 130 980F6842FEBB93BA 130 980F6842FEBB93BA
 144 980F6842FEBB93BA 144 980F6842FEBB93BA
 132 A2E6E431D426B1E7 132 A2E6E431D426B1E7
 142 A2E6E431D426B1E7 142 A2E6E431D426B1E7
 89 B79AE2610DD89D4C 89 B79AE2610DD89D4C
 121 B79AE2610DD89D4C 121 B79AE2610DD89D4C
 152 B79AE2610DD89D4C 152 B79AE2610DD89D4C
 134 C43194B3487F5A36 134 C43194B3487F5A36
 143 C43194B3487F5A36 143 C43194B3487F5A36
 128 E40A7944DBDE6DAE 128 E40A7944DBDE6DAE
 135 E40A7944DBDE6DAE 135 E40A7944DBDE6DAE |
 79 E68AA26A841A86FA 79 E68AA26A841A86FA
 111 E68AA26A841A86FA 111 E68AA26A841A86FA
 147 E68AA26A841A86FA 147 E68AA26A841A86FA
 149 E68AA26A841A86FA 149 E68AA26A841A86FA
 162 E68AA26A841A86FA 162 E68AA26A841A86FA
 73 F7E62F36F8DB5AE6 73 F7E62F36F8DB5AE6
 105 F7E62F36F8DB5AE6 105 F7E62F36F8DB5AE6
 139 F7E62F36F8DB5AE6 139 F7E62F36F8DB5AE6
 140 F7E62F36F8DB5AE6 140 F7E62F36F8DB5AE6
 141 F7E62F36F8DB5AE6 141 F7E62F36F8DB5AE6
 161 F7E62F36F8DB5AE6 161 F7E62F36F8DB5AE6 |
 |
|
Copyright Notice: You must get permission from the respective author before reproduction.
| |
